Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
Search Results For - Vulnerability
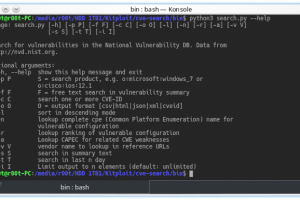
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Security researchers have discovered a new privilege-escalation vulnerability in Linux kernel that could allow a local attacker to execute code on the affected...
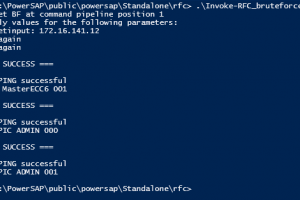
PowerSAP is a simple powershell re-implementation of popular & effective techniques of all public tools such as Bizploit, Metasploit auxiliary modules, or...
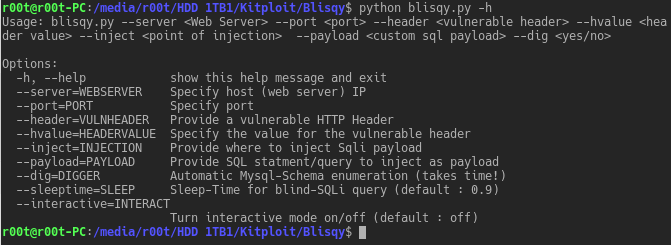
A slow data siphon for MySQL/MariaDB using bitwise operation on printable ASCII characters, via a blind-SQL injection. Usage USAGE: blisqy.py --server <Web...
WINspect is part of a larger project for auditing different areas of Windows environments. It focuses on enumerating different parts of a Windows machine...
Do you know—United States Government has banned federal agencies from using Kaspersky antivirus software over spying fear? Though there’s no solid...
A severe programming error has been discovered in Apple’s latest macOS High Sierra 10.13 that exposes passwords of encrypted Apple File System (APFS)...
Hey Guys, In this video i show you a great tool called Yuki Chan. The Yuki Chan is an Automated Penetration Testing tool this tool will auditing all standard...
Hey Guys, In this video i show you a great Security Auditing Tool for Unix/Linux Systems called Lynis. Lynis is an open source security auditing tool. Used by...