M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
Search Results For - VPN
Tool to check if a given IP is a node tor or an open proxy. Why? Sometimes all your throttles are not enough to stop brute force attacks or any kind of massive...
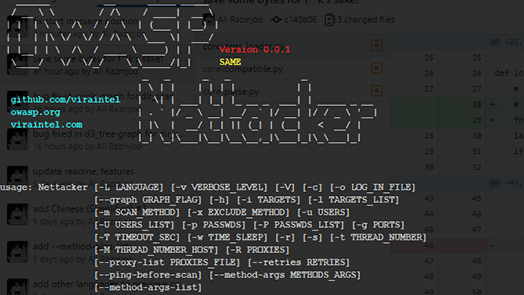
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
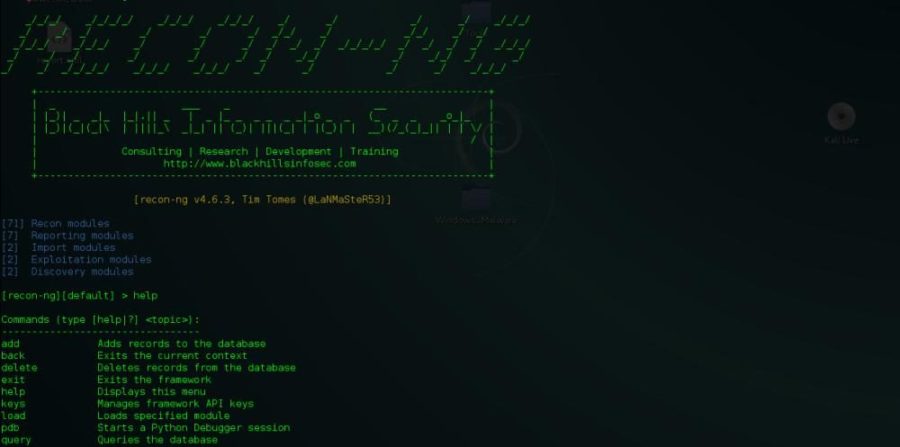
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience...
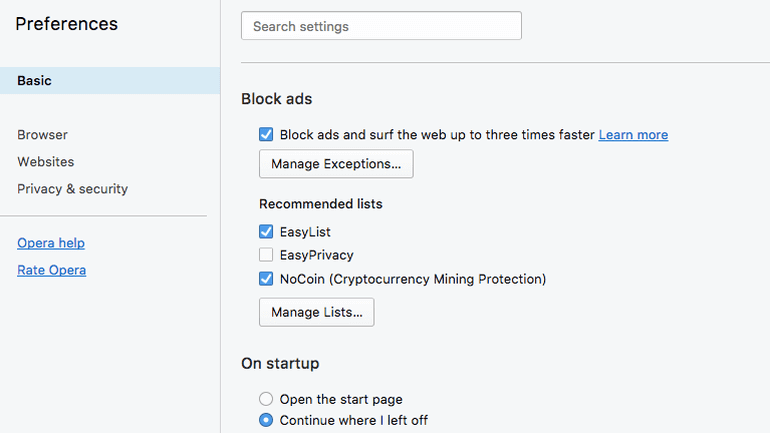
Norwegian browser maker Opera has launched the beta version of Opera 50, the first popular browser to integrate a built-in cryptocurrency-mining blocker. The...
Take back your privacy. Lose yourself in the haystack. Your ISP is most likely tracking your browsing habits and selling them to marketing agencies (albeit...
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
Google has explicitly rejected them from the Play Store. Identify Airpush? The current advertisement scourge is ad-infused lock screens, which have shown up in...
Today, 9 November 2017, WikiLeaks publishes the source code and development logs to Hive, a major component of the CIA infrastructure to control its malware...