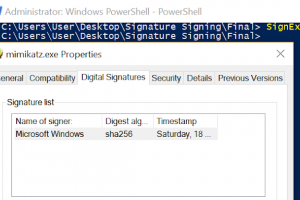
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
Search Results For - Twitter
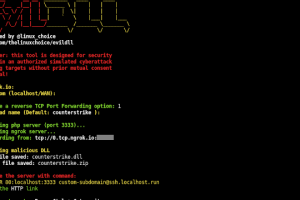
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Malicious DLL (Win Reverse Shell) generator for DLL Hijacking Features:...
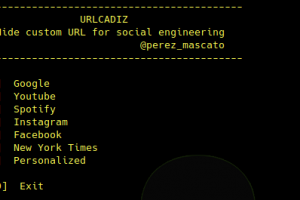
[sc name=”ad_1″] A simple script to generate a hidden url for social engineering. Legal disclaimer: Usage of URLCADIZ for attacking targets without...
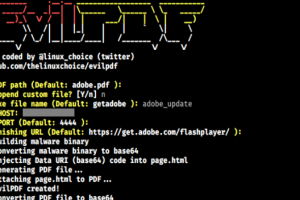
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Hiding executable files in PDF documents Legal disclaimer: Usage of...
[sc name=”ad_1″] RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without...
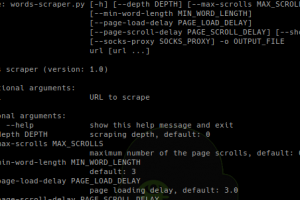
[sc name=”ad_1″] Selenium based web scraper to generate passwords list. Installation # Download Firefox webdriver from $ tar xzf geckodriver...
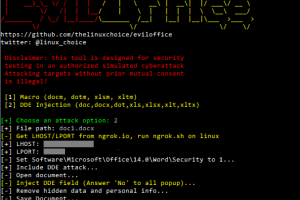
[sc name=”ad_1″] Win python script to inject Macro and DDE code into Excel and Word documents (reverse shell) Features: Inject malicious Macro on...
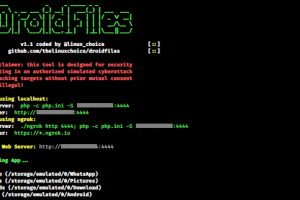
[sc name=”ad_1″] Get files from Android directories, internal and external storage (Pictures, Downloads, Whatsapp, Videos, …) Legal...
[sc name=”ad_1″] Project iKy is a tool that collects information from an email and shows results in a nice visual interface. Visit the Gitlab Page...
[sc name=”ad_1″] Working and learning have gone remote, and we have to come to terms with this new reality. Nowadays, several organizations allow...