Critically, both OS updates address the KRACK Wi-Fi vulnerability for any devices. It is a dangerous vulnerability in the WPA2 Wi-Fi assurance standard that...
Search Results For - Traffic
An unknown hacker has hijacked Coinhive’s DNS server and modified the legitimate Coinhive JavaScript in-browser miner with a malicious one that mined Monero...
DUHK (Don’t Use Hard-coded Keys) is a new crypto implementation attack that could enable attackers to obtain secret keys that secure VPN (Virtual Private...
DNS over TLS is a protocol where DNS inquiries will be encrypted to the equivalent level as HTTPS and therefore a DNS can’t actually log or see the websites...
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...
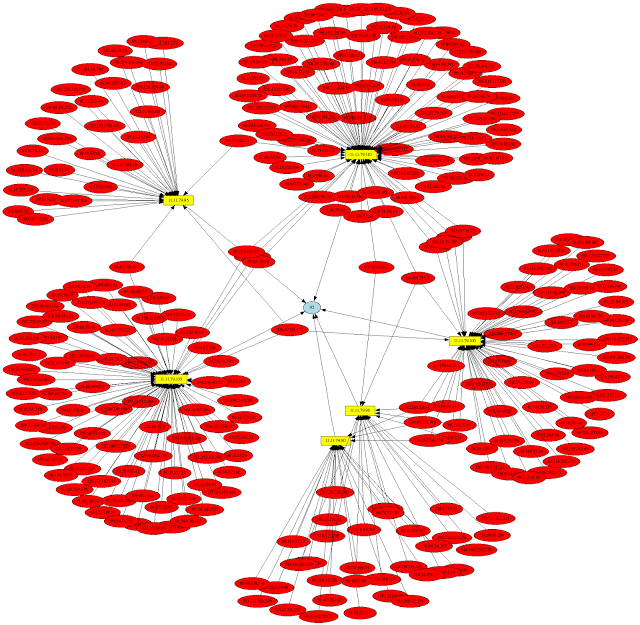
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
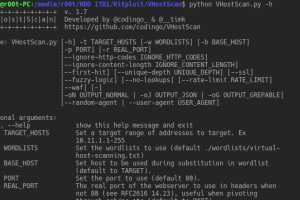
A virtual host scanner that can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. First presented at SecTalks BNE in...
The Port Scan Attack Detector psad is a lightweight system daemon written in is designed to work with Linux iptables/ip6tables/firewalld firewalling code to...
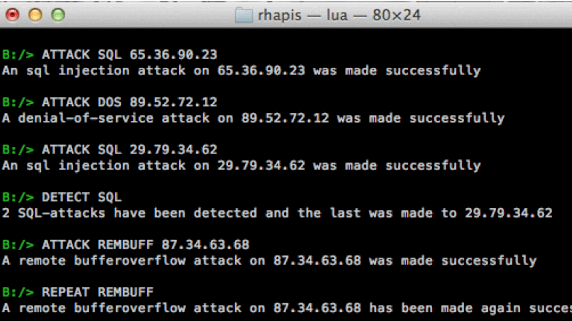
Network intrusion detection systems simulator. RHAPIS provides a simulation environment through which user is able to execute any IDS operation. Basic Usage...
There is terrible news for all OnePlus lovers. Your OnePlus handset, running OxygenOS—the company’s custom version of the Android operating system, is...