Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account...
Search Results For - Threat
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
This hack was not conducted in a laboratory, but on a 757 gathered at the airport in Atlantic City, N.J. And the real hack happened over a year ago. We are...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
Security firm Positive Technologies lists being able to execute unsigned code on computers working the IME through USB. The fully fleshed-out details of the...
The Google Play store has made headlines recently when cyber criminals were able to hack in and post a fake WhatsApp messenger update for download. More than a...
Apple’s privacy signs do not spread to the thousands of app developers who will gain access to facial data in order to increase entertainment features for...
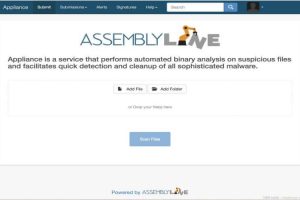
Assemblyline is a scalable distributed file analysis framework. It is designed to process millions of files per day but can also be installed on a single box...
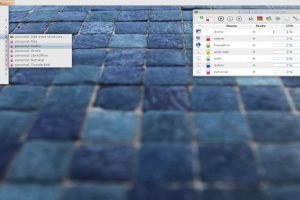
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
News reported in June that McAfee was amongst several Western technology organizations that had acceded in recent years to larger demands by Moscow for access...