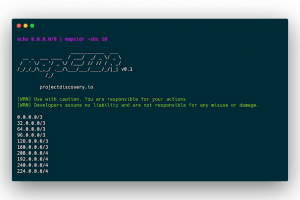
[sc name=”ad_1″] Small utility program to perform multiple operations for a given subnet/CIDR ranges. The tool was developed to ease load...
Search Results For - Subnet
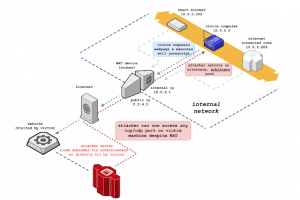
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
[sc name=”ad_1″] webscan is a browser-based network IP scanner and local IP detector. It detects IPs bound to the user/victim by listening on an...
[sc name=”ad_1″] Collection of PowerShell functions a Red Teamer may use to collect data from a machine or gain access to a target. I added ps1...
[sc name=”ad_1″] Takeover AWS ips and have a working POC for Subdomain Takeover. Idea is simple Get subdomains. Do reverse lookups to only save AWS...
[sc name=”ad_1″] Nuubi Tools: Information-ghatering|Scanner|Recon Options: -h/--help | Show help message and exit Arguments: -b/--banner | Banner...
[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
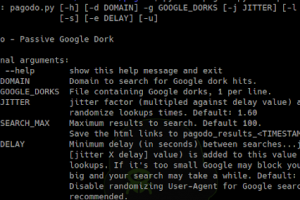
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
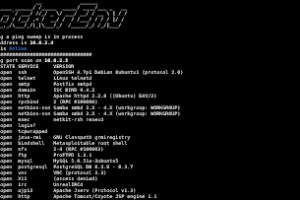
[sc name=”ad_1″] hackerEnv is an automation tool that quickly and easily sweep IPs and scan ports, vulnerabilities and exploit them. Then, it hands...
[sc name=”ad_1″] FastNetMon – A high performance DoS/DDoS load analyzer built on top of multiple packet capture engines (NetFlow, IPFIX...