[sc name=”ad_1″] SKA allows you to implement a very simple and fast karma attack. You can sniff probe requests to choice the fake AP name or, if...
Search Results For - Screenshot
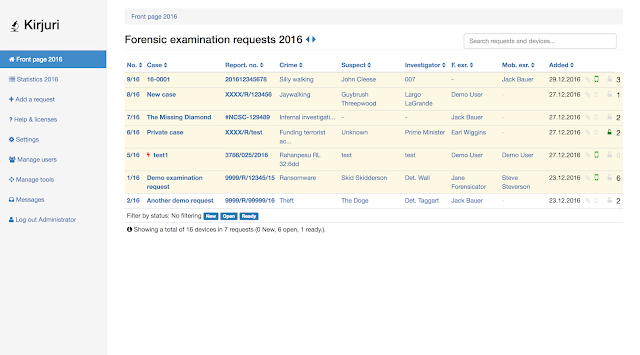
[sc name=”ad_1″] Kirjuri is a simple php/mysql web application for managing physical forensic evidence items. It is intended to be used as a...
[sc name=”ad_1″] Introduction Dr. ROBOT is a tool for Domain Reconnaissance and Enumeration. By utilizing containers to reduce the overhead of...
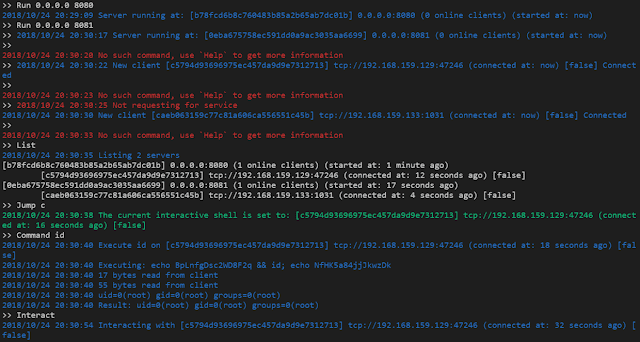
[sc name=”ad_1″] A modern multiple reverse shell sessions/clients manager via terminal written in go. Features Multiple service listening port...
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
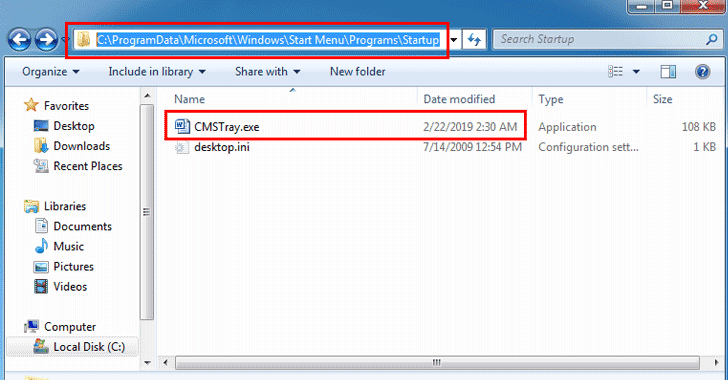
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
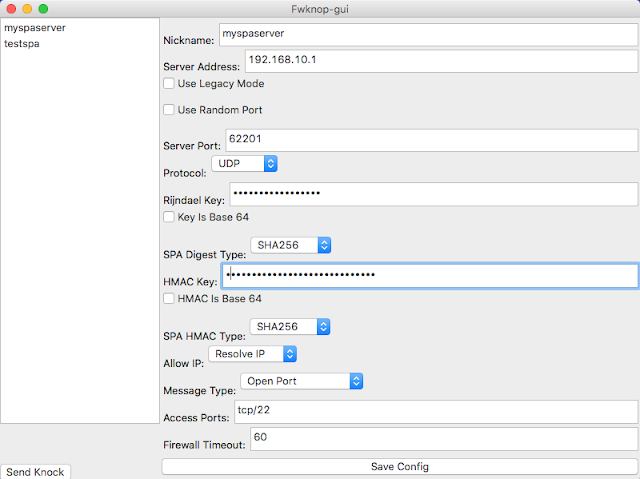
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
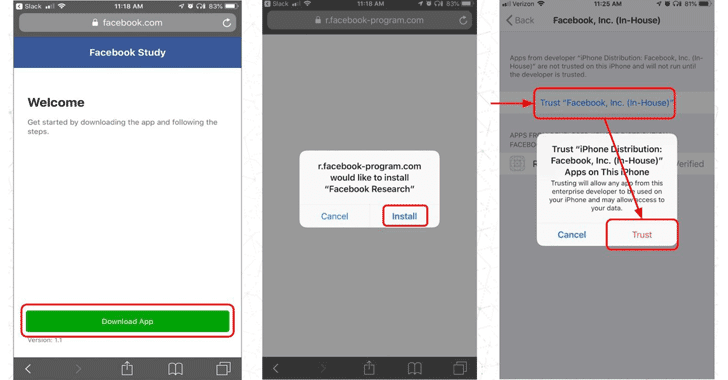
[sc name=”ad_1″] If you are thinking that Facebook is sitting quietly after being forced to remove its Onavo VPN app from Apple’s App Store...
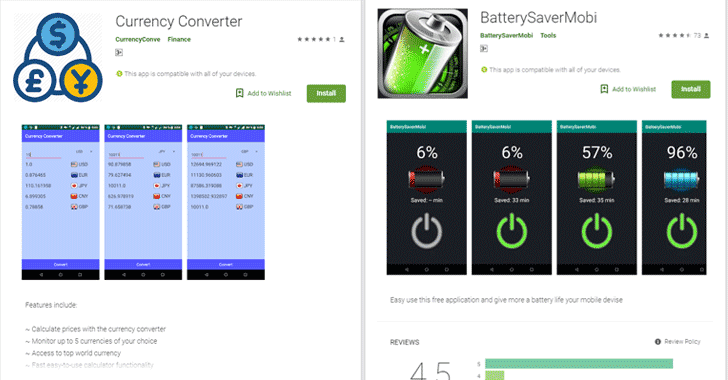
[sc name=”ad_1″] Even after so many efforts by Google for preventing its Play Store from malware, shady apps somehow managed to fool its anti...
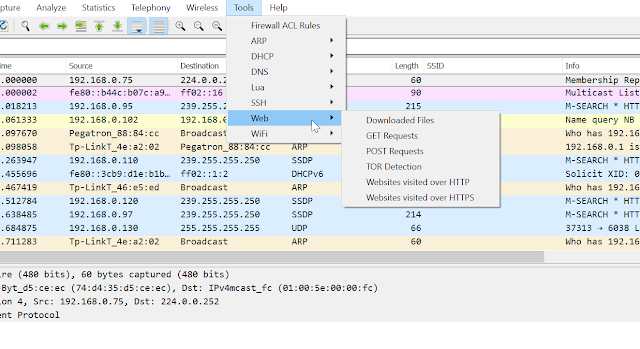
[sc name=”ad_1″] PA Toolkit is a collection of traffic analysis plugins to extend the functionality of Wireshark from a micro-analysis tool and...