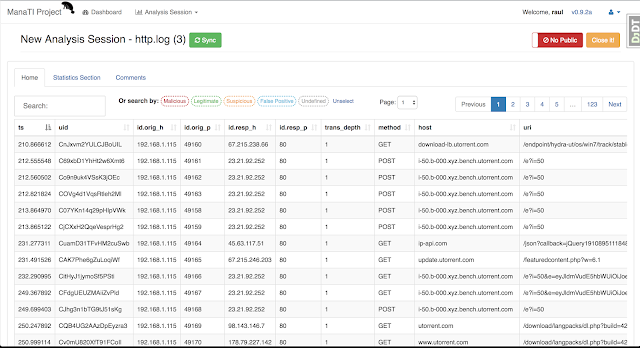
[sc name=”ad_1″] Machine Learning for Threat Intuitive Analysis The goal of the ManaTI project is to develop machine learning techniques to assist...
Search Results For - SSH
[sc name=”ad_1″] This tool launches attack on k8s cluster from within. That means you already need to have an access with permission to deploy pods...
[sc name=”ad_1″] flare-emu marries IDA Pro’s binary analysis capabilities with Unicorn’s emulation framework to provide the user with an easy to...
[sc name=”ad_1″] Anteater is an open framework to prevent the unwanted merging of nominated strings, filenames, binaries, depreciated functions...
[sc name=”ad_1″] Dolos Cloak is a python script designed to help network penetration testers and red teamers bypass 802.1x solutions by using an...
[sc name=”ad_1″] Introduction Dr. ROBOT is a tool for Domain Reconnaissance and Enumeration. By utilizing containers to reduce the overhead of...
[sc name=”ad_1″] Mondoo is infrastructure and security analytics your cloud-native applications. By removing the code literacy, we strive to make...
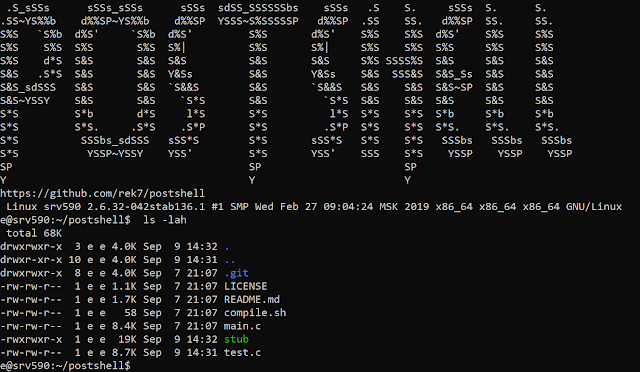
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY...
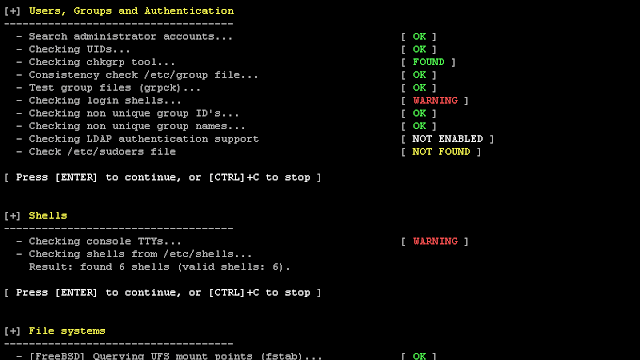
[sc name=”ad_1″] We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of...
[sc name=”ad_1″] The popular SSH client program PuTTY has released the latest version of its software that includes security patches for 8 high...