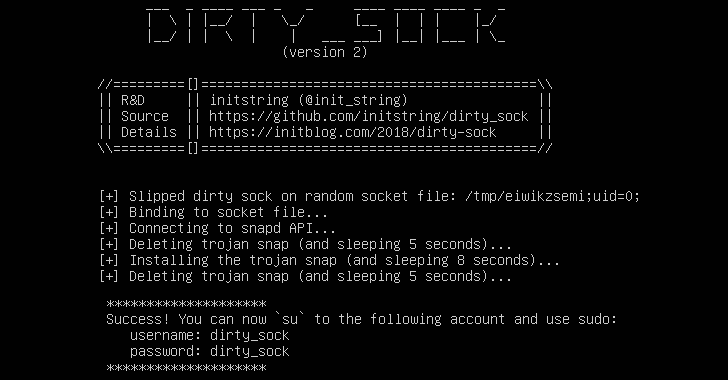
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
Search Results For - SSH
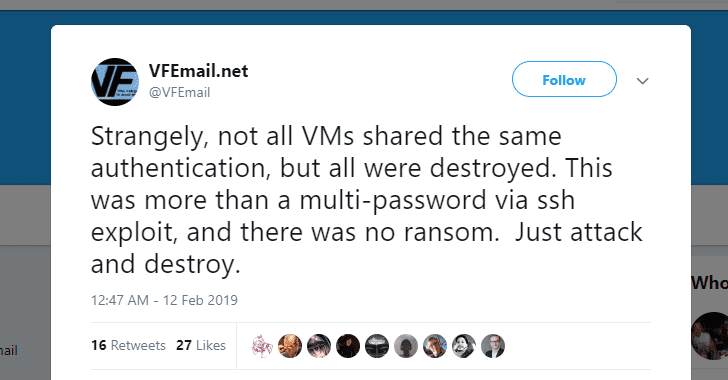
[sc name=”ad_1″] What could be more frightening than a service informing you that all your data is gone—every file and every backup servers are...
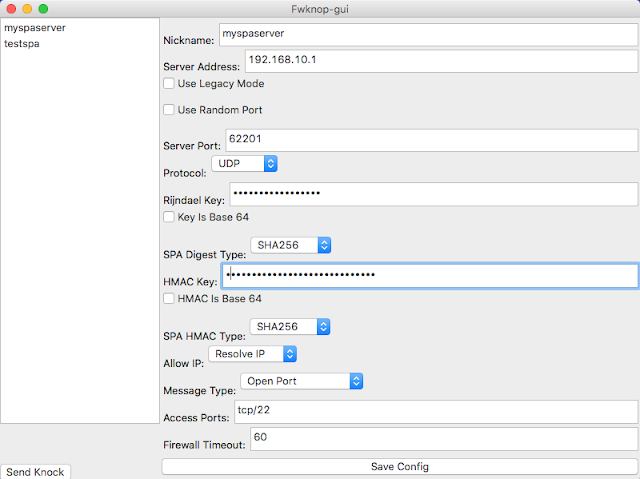
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] A set of 36-year-old vulnerabilities has been uncovered in the Secure Copy Protocol (SCP) implementation of many client...
[sc name=”ad_1″] Shodan is a search engine on the internet where you can find interesting things all over the world. For example, we can find...
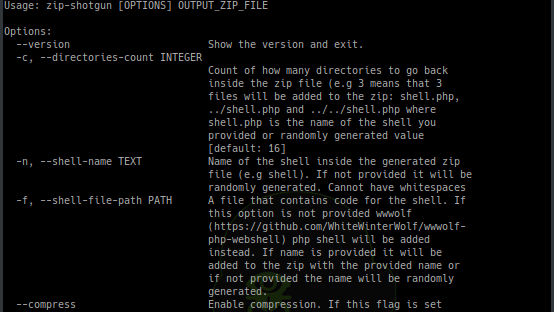
[sc name=”ad_1″] Utility script to test zip file upload functionality (and possible extraction of zip files) for vulnerabilities. Idea for this...
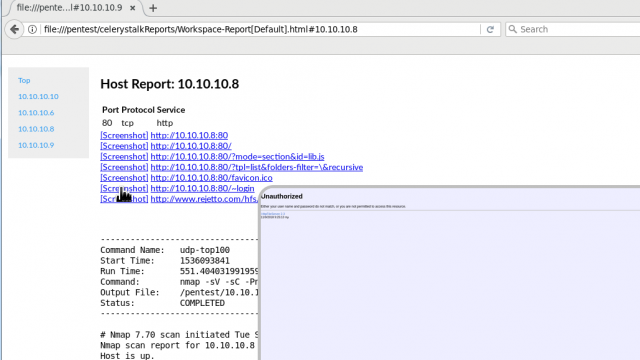
[sc name=”ad_1″] celerystalk helps you automate your network scanning/enumeration process with asynchronous jobs (aka tasks) while retaining full...
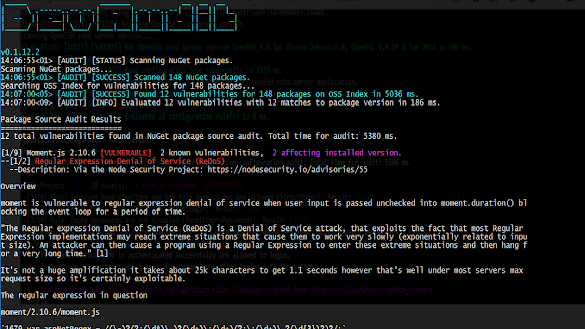
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...
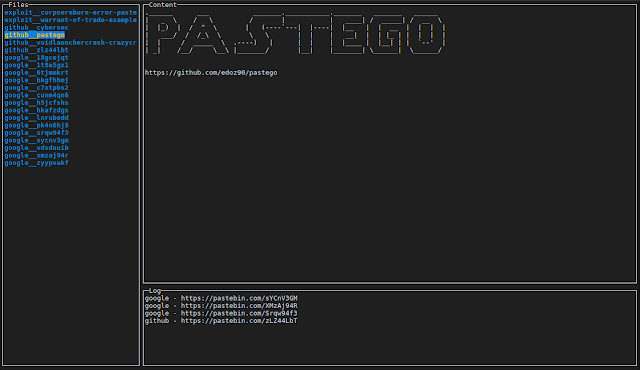
Scrape/Parse Pastebin using GO and grammar expression (PEG). Installation $ go get -u github.com/edoz90/pastego Usage Search keywords are case sensitive...
Use open source tools and network intelligence to help organizations with attack surface discovery and identification of security vulnerabilities...