OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
Search Results For - SSH server
The 2016 election hack is back in the news. With great efforts, a Russian hacker was arrested and upon interrogation, he revealed that he was hired by the...
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...
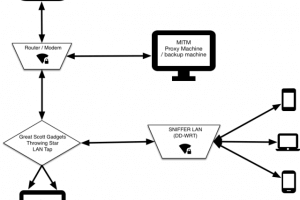
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
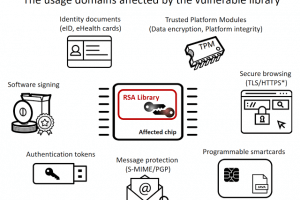
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
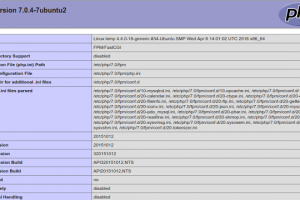
Check current PHP configuration for potential security flaws. Simply access this file from your webserver or run on CLI. Author This software was written by...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...