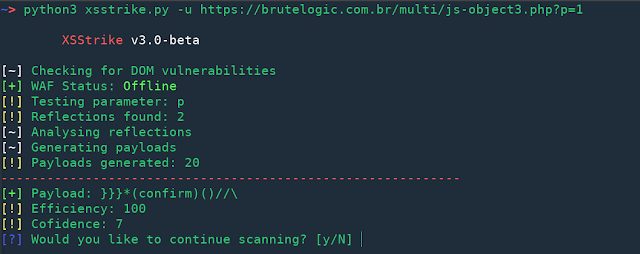
Why XSStrike? Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared...
Search Results For - Research
An Indian security researcher has discovered a highly critical flaw in X.Org Server package that impacts OpenBSD and most Linux distributions, including...
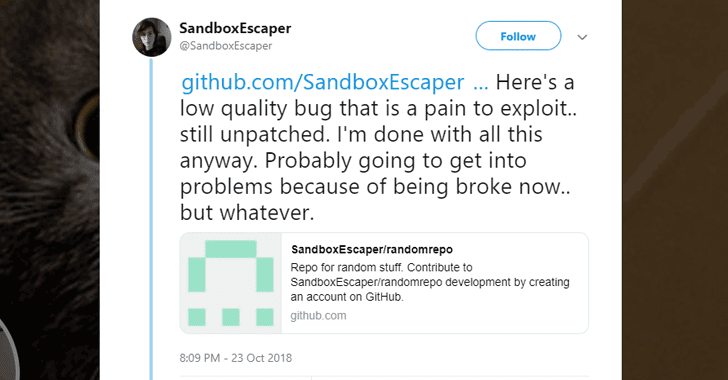
A security researcher with Twitter alias SandboxEscaper—who two months ago publicly dropped a zero-day exploit for Microsoft Windows Task Scheduler—has...
TLS-Scanner is a tool created by the Chair for Network and Data Security from the Ruhr-University Bochum to assist pentesters and security researchers in the...
Bashark aids pentesters and security researchers during the post-exploitation phase of security audits. Usage To launch Bashark on compromised host, simply...
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media...
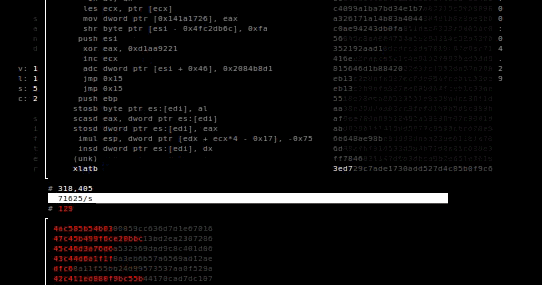
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
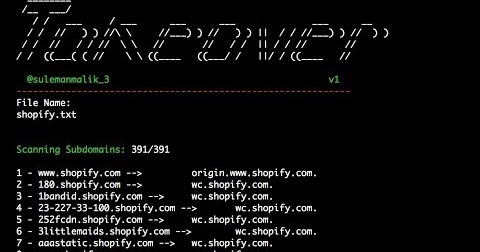
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...
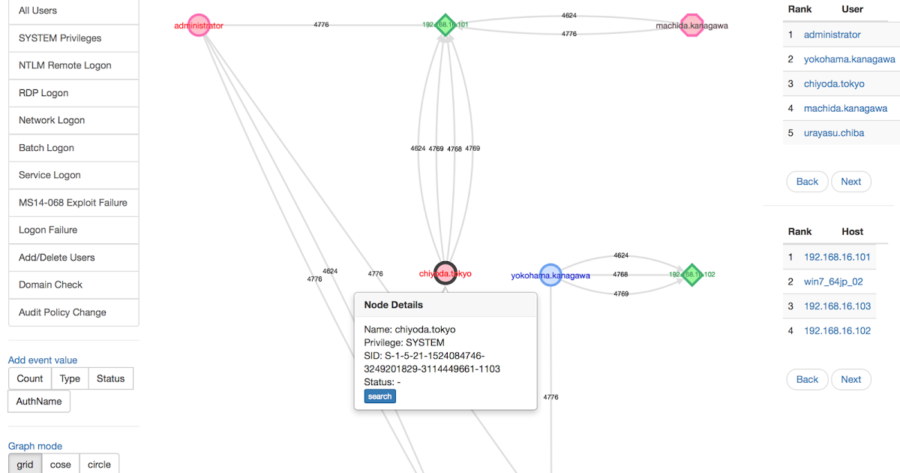
Investigate malicious logon by visualizing and analyzing Windows active directory event logs. Concept LogonTracer associates a host name (or an IP address) and...
Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...