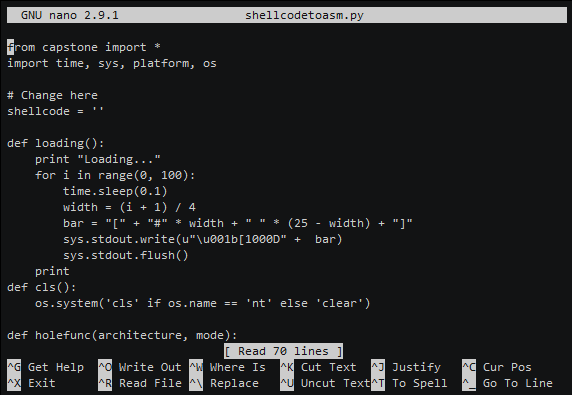
Transform your Shellcode to Assembly (ARM, ARM64, MIPS, PPC, X86) Replace in shellcodetoasm.py with your shellcode. shellcode = '' Installation git clone...
Search Results For - Requirements
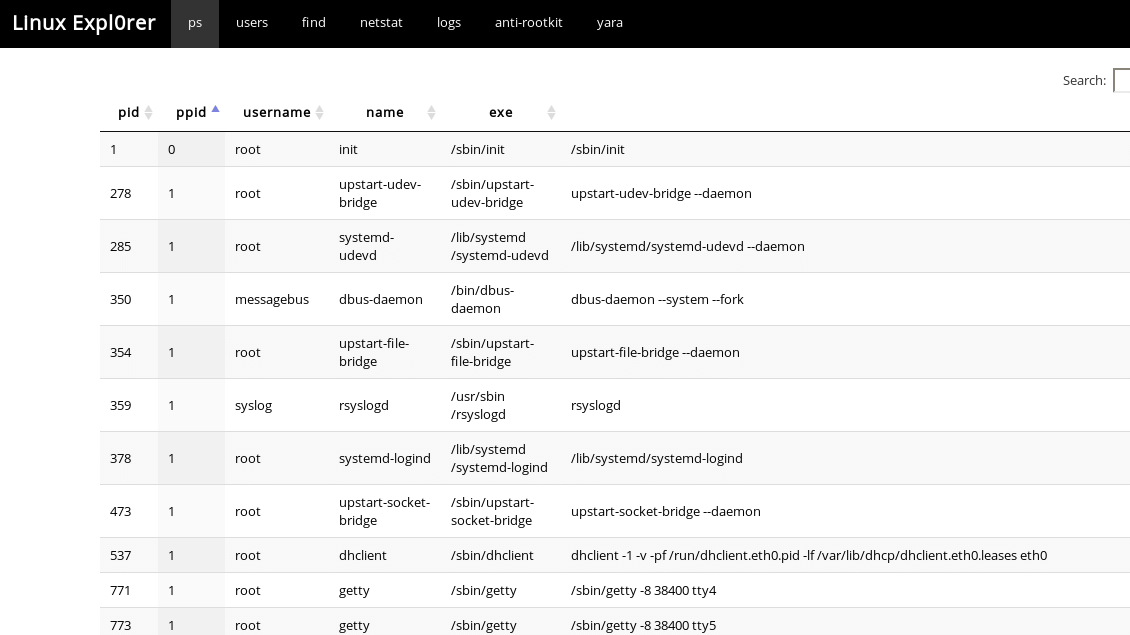
Easy-to-use live forensics toolbox for Linux endpoints written in Python & Flask. Capabilities ps View full process list Inspect process memory map &...
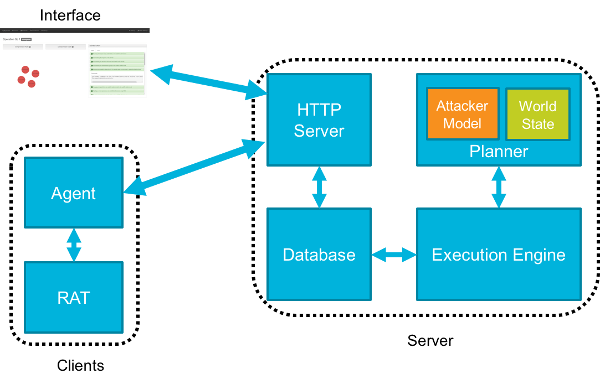
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during...
Aletheia is a steganalysis tool for the detection of hidden messages in images. The goal of steganalysis is to identify suspected packages, determine whether...
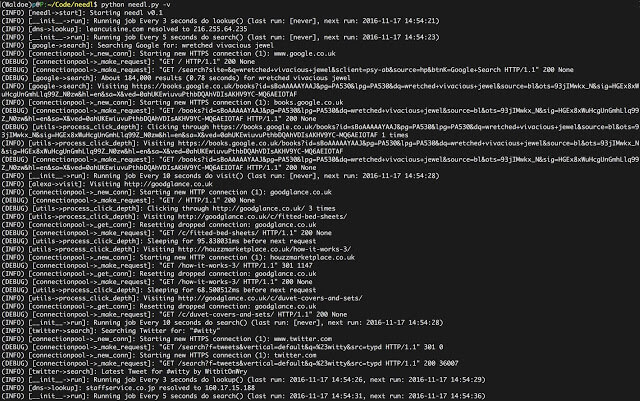
Take back your privacy. Lose yourself in the haystack. Your ISP is most likely tracking your browsing habits and selling them to marketing agencies (albeit...
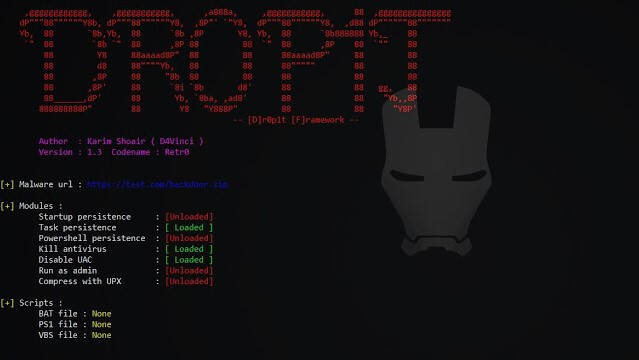
Have you ever heard about trojan droppers ? In short dropper is type of malware that downloads other malwares and Dr0p1t gives you the chance to create a...
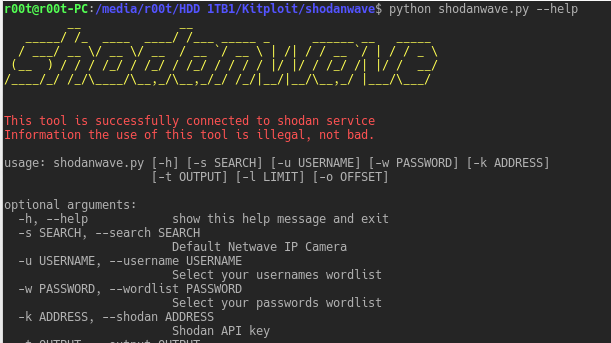
Shodanwave is a tool for exploring and obtaining information from cameras specifically Netwave IP Camera. The tool uses a search engine called shodan that...
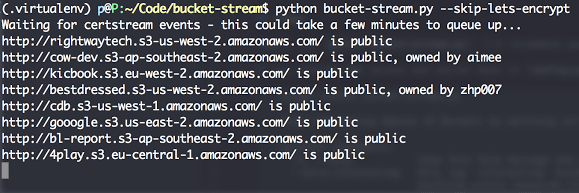
Some quick tips if you use S3 buckets: Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com. Set appropriate permissions and...
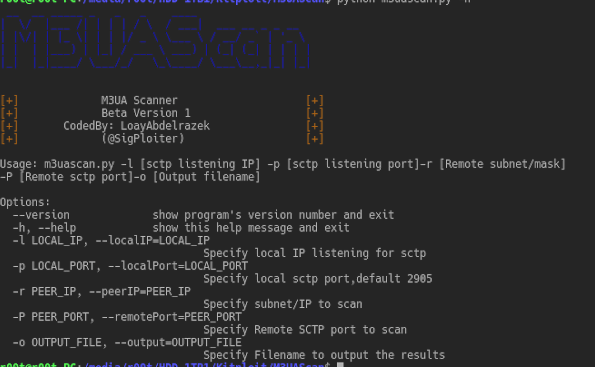
A Scanner for M3UA protocol to detect Sigtran supporting nodes M3UA stands for MTP Level 3 (MTP3) User Adaptation Layer as defined by the IETF SIGTRAN working...
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...