[sc name=”ad_1″] Microsoft today, on its year-end December Patch Tuesday, released security updates to patch a total 39 vulnerabilities its Windows...
Search Results For - Remote Command Execution
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
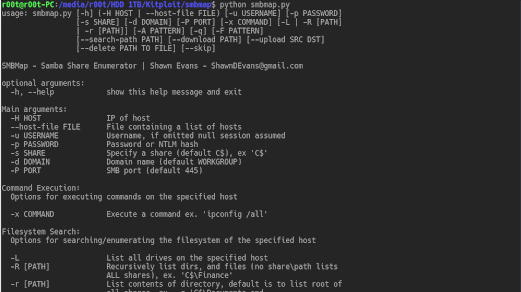
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download...
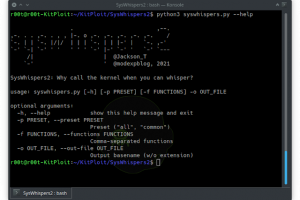
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
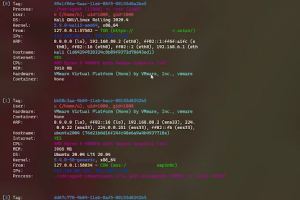
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
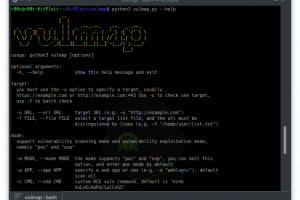
[sc name=”ad_1″] Vulmap is a vulnerability scanning tool that can scan for vulnerabilities in Web containers, Web servers, Web middleware, and CMS...
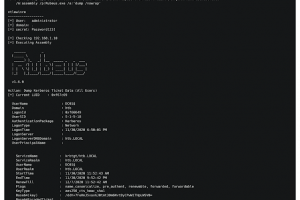
[sc name=”ad_1″] A sharpen version of CrackMapExec. This tool is made to simplify penetration testing of networks and to create a swiss army knife...
[sc name=”ad_1″] About Ghost Framework Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...