[sc name=”ad_1″] Security researchers have uncovered a new variant of the infamous Mirai Internet of Things botnet, this time targeting embedded...
Search Results For - Remote Command Execution
[sc name=”ad_1″] Libssh2, a popular open source client-side C library implementing the SSHv2 protocol, has released the latest version of its...
[sc name=”ad_1″] If you are a Counter-Strike gamer, then beware, because 39% of all existing Counter-Strike 1.6 game servers available online are...
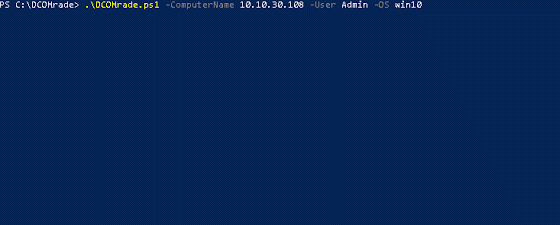
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for...
[sc name=”ad_1″] It’s 2019, and just opening an innocent looking office document file on your system can still allow hackers to compromise...
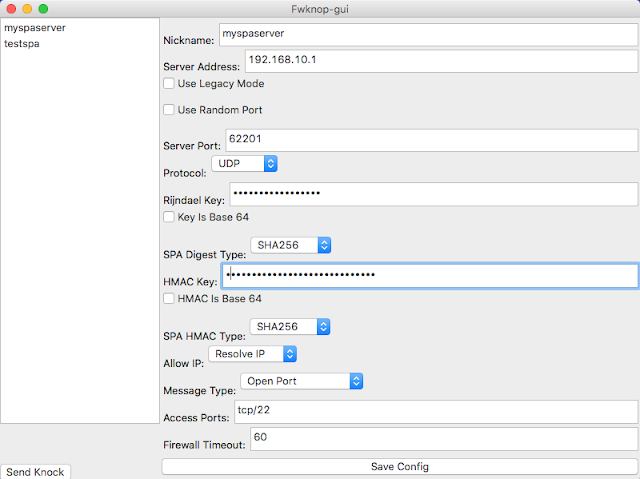
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
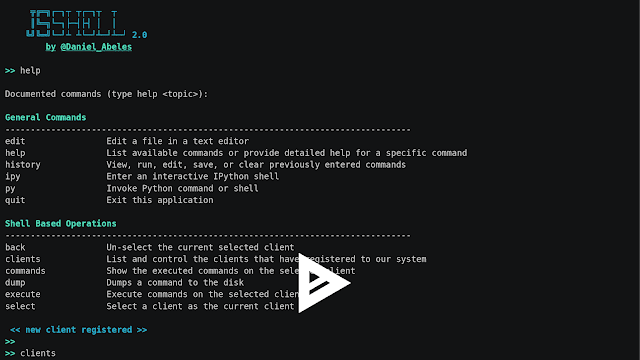
[sc name=”ad_1″] An interactive multi-user web based javascript shell. It was initially created in order to debug remote esoteric browsers during...
[sc name=”ad_1″] Microsoft today issued an out-of-band security update to patch a critical zero-day vulnerability in Internet Explorer (IE) Web...
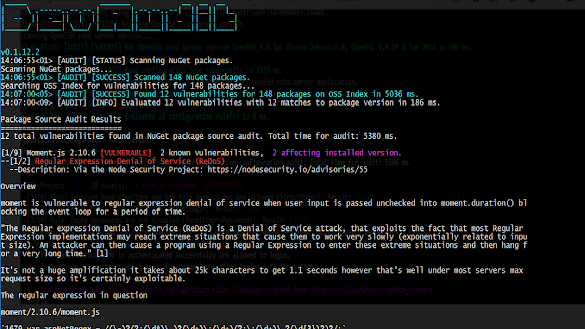
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...