[sc name=”ad_1″] nginx Docker image secure by default. Avoid the hassle of following security best practices each time you need a web server or...
Search Results For - Remote Access
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
[sc name=”ad_1″] teler is an real-time intrusion detection and threat alert based on web log that runs in a terminal with resources that we collect...
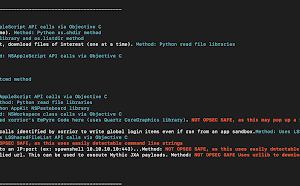
[sc name=”ad_1″] MacC2 is a macOS post exploitation tool written in python that uses Objective C calls or python libraries as opposed to command...
[sc name=”ad_1″] GWTMap is a tool to help map the attack surface of Google Web Toolkit (GWT) based applications. The purpose of this tool is to...
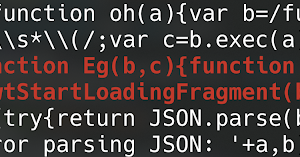
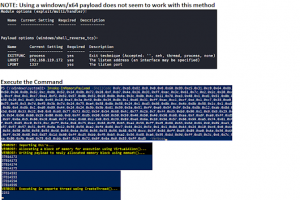
[sc name=”ad_1″] Collection of PowerShell functions a Red Teamer may use to collect data from a machine or gain access to a target. I added ps1...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
[sc name=”ad_1″] What’s AutoGadgetFS ? AutoGadgetFS is an open source framework that allows users to assess USB devices and their associated...
[sc name=”ad_1″] RmiTaste allows security professionals to detect, enumerate, interact and attack RMI services by calling remote methods with...
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...