[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
Search Results For - Remote Access
[sc name=”ad_1″] Many usefull offensive CSharp Projects wraped into Powershell for easy usage. Why? In my personal opinion offensive Powershell is...
[sc name=”ad_1″] OpenVPN is open-source commercial software that implements virtual private network techniques to create secure point-to-point or...
[sc name=”ad_1″] You’ve always been warned not to share remote access to your computer with any untrusted people for many reasons—it’s...
[sc name=”ad_1″] The United States Department of Justice (DoJ) announced Wednesday its effort to “map and further disrupt” a botnet...
[sc name=”ad_1″] A massive government data belonging to the Oklahoma Department of Securities (ODS) was left unsecured on a storage server for at...
Armor is a simple Bash script designed to create encrypted macOS payloads capable of evading antivirus scanners. Below is an example gif of Armor being used...
A 21-year-old Kentucky man who previously pleaded guilty to developing, marketing, and selling an infamous remote access trojan (RAT) called LuminosityLink has...
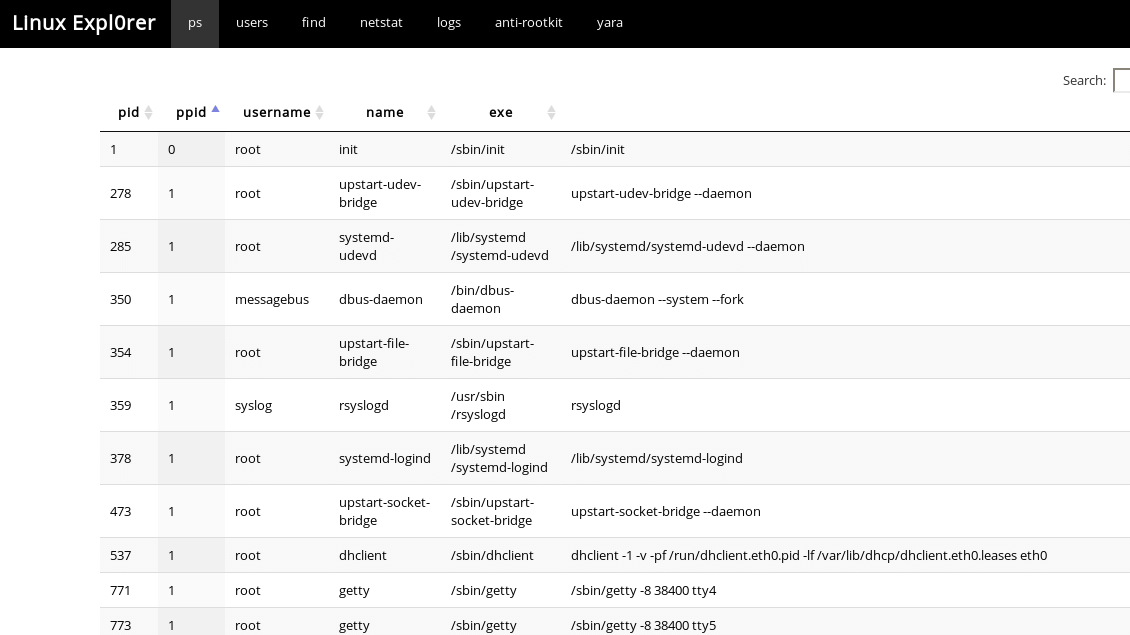
Easy-to-use live forensics toolbox for Linux endpoints written in Python & Flask. Capabilities ps View full process list Inspect process memory map &...
Apple is one of the biggest companies today, but its devices are not free from issues. Recently, it was reported that the company’s HomeKit software used to...