The corporation says that version 390 of its GPU video driver will be the last to carry 32-bit platforms. “Later driver release reports will not operate, nor...
Search Results For - Red Team
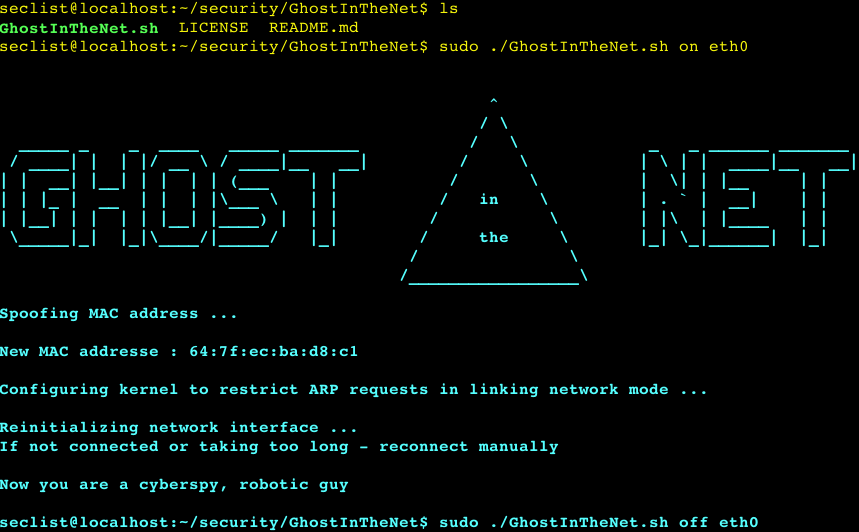
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
A new plug-in called “Looking Glass” discovered in each instance of the new Firefox Quantum browser. It was turned off by default, but users were still scared...
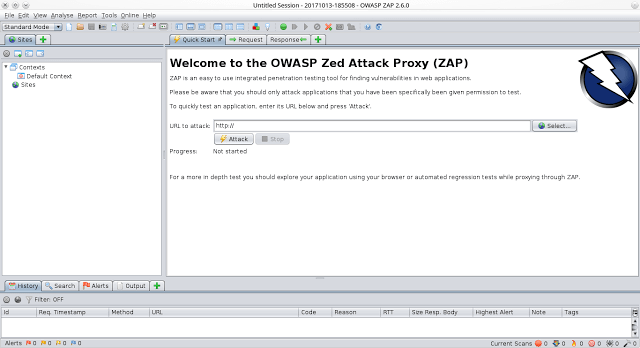
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It...
The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
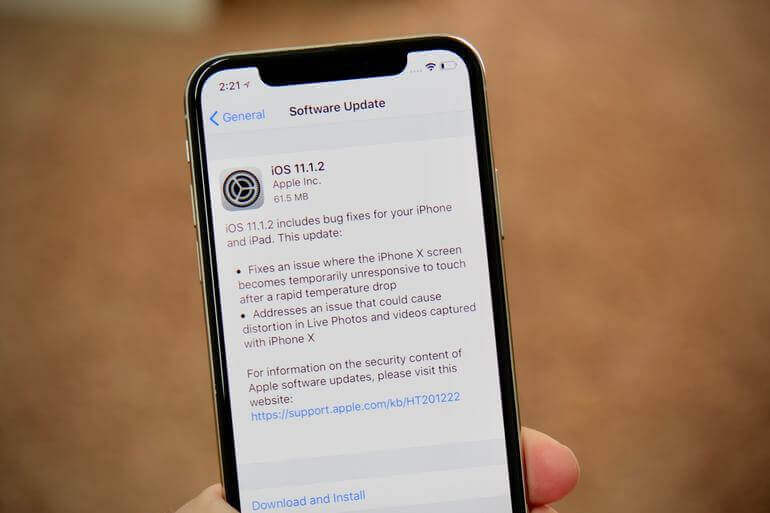
Google’s Project Zero iOS bug hunter Ian Beer has released details about an iOS 11 exploit that could offer up a jailbreak for iOS 11.1.2. Beer last week...
Gone are the days when airports were considered to be safe. A recent activity left Australians shocked when a professional hacker got hacked into Peth’s...
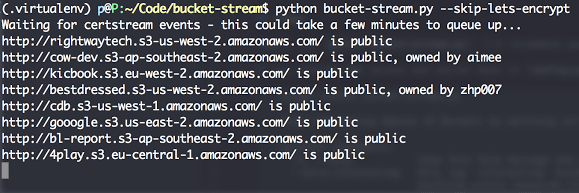
Some quick tips if you use S3 buckets: Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com. Set appropriate permissions and...
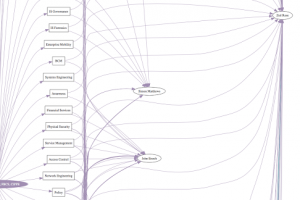
An OSINT tool that allows you to draw out relationships between people on LinkedIn via endorsements/skills. Check out the example (digraph), which is based on...