Xerosploit is a penetration testing toolkit whose goal is to perform man in the middle attacks for penetration testing purposes. It brings various modules...
Search Results For - Python 3
Attack vectors There are 4 attack vectors available: beacon creds meterpreter meterpreter-grant For the ‘creds’ method, macphish can generate the Applescript...
The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines...
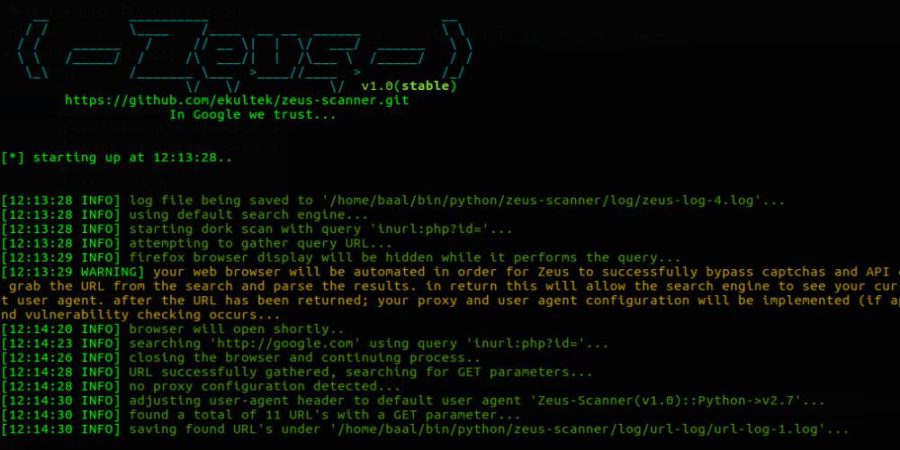
Zeus is a advanced dork searching tool that is capable of bypassing search engine API calls, search engine captchas, and IP address blocking from sending many...
Windows’ BITS service is a middleman for your download jobs. You start a BITS job, and from that point on, BITS is responsible for the download. But what if we...
Wfuzz is a tool designed for bruteforcing Web Applications, it can be used for finding resources not linked (directories, servlets, scripts, etc), bruteforce...
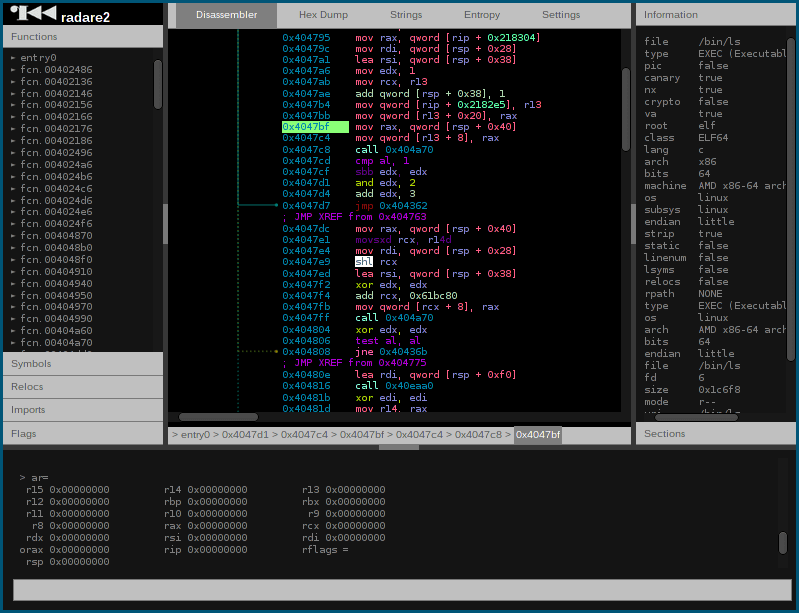
r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files. The radare project started as a forensics...
Tinfoleak is a simple Python script that allow to obtain detailed information about a Twitter user activity Detailed information about any Twitter user: basic...
A BLE scanner for “smart” devices hacking based on the bluepy library, dead easy to use because retarded devices should be dead easy to hack. How to...
The UEFI firmware parser is a simple module and set of scripts for parsing, extracting, and recreating UEFI firmware volumes. This includes parsing modules for...