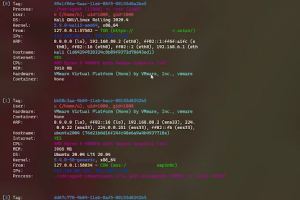
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
Search Results For - Post-Exploitation
[sc name=”ad_1″] About Ghost Framework Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely...
[sc name=”ad_1″] DeimosC2 is a post-exploitation Command & Control (C2) tool that leverages multiple communication methods in order to control...
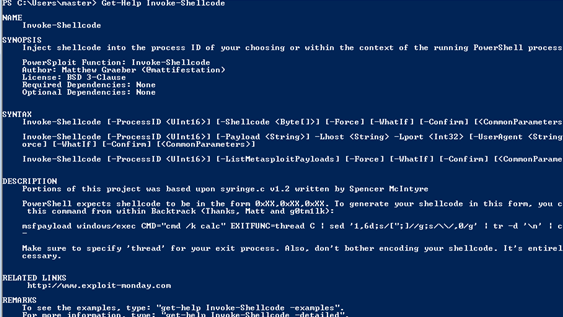
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
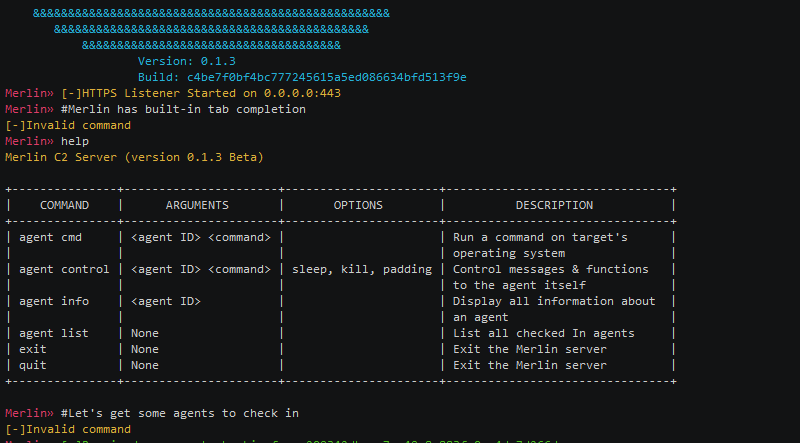
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
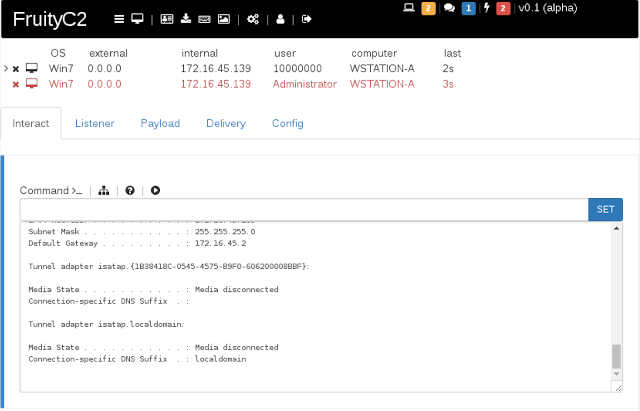
This is the initial release for FruityC2 (alpha version). Can be installed on any linux system, but the installation scripts are made for Debian based systems...
[sc name=”ad_1″] The Nethive Project provides a Security Information and Event Management (SIEM) insfrastructure empowered by CVSS automatic...
[sc name=”ad_1″] Many usefull offensive CSharp Projects wraped into Powershell for easy usage. Why? In my personal opinion offensive Powershell is...