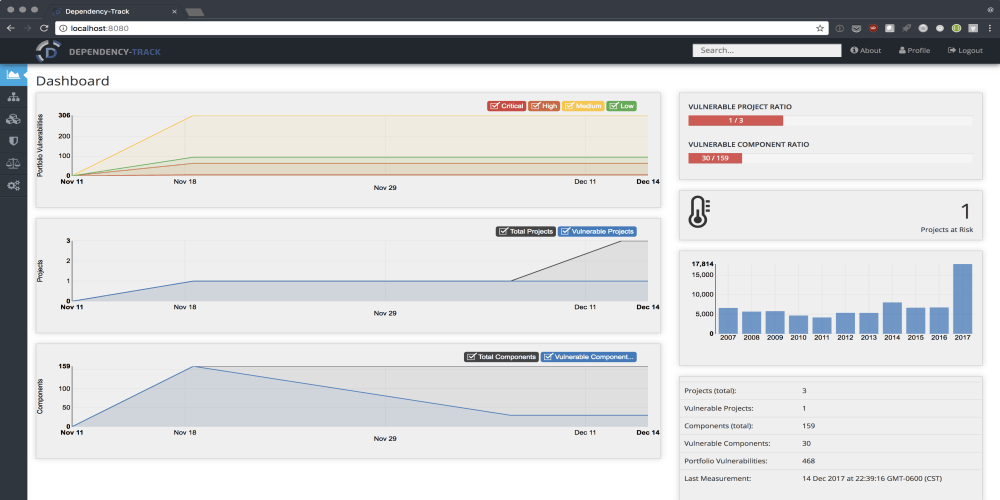
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
Search Results For - Opera
[sc name=”ad_1″] Hacking a Wi-Fi network using Kali Linux needs a wireless card that support monitor mode and packet injection. Not all wireless...
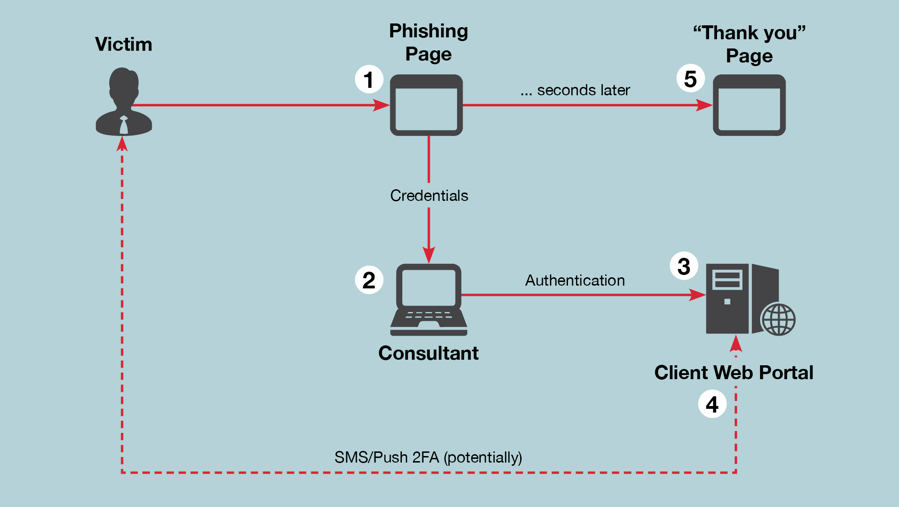
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
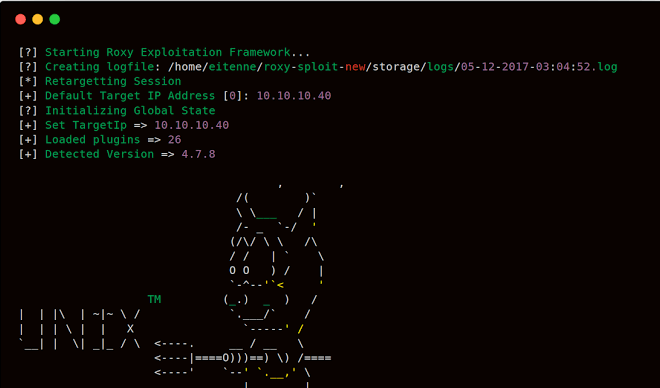
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
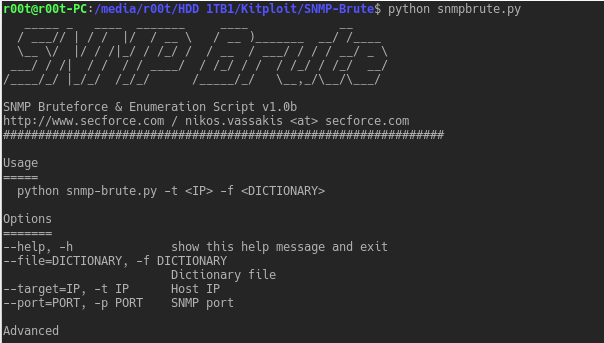
SNMP brute force, enumeration, CISCO config downloader and password cracking script. Listens for any responses to the brute force community strings...
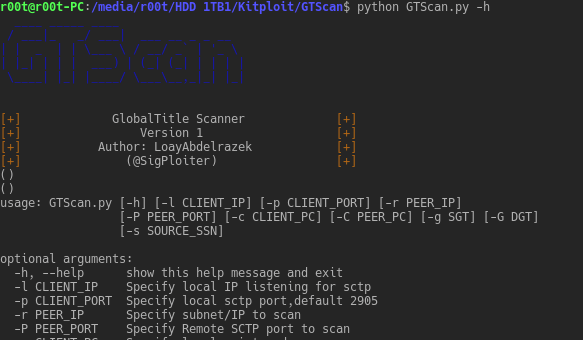
The Nmap Scanner for Telco. With the current focus on telecom security, there used tools in day to day IT side penetration testing should be extended to...
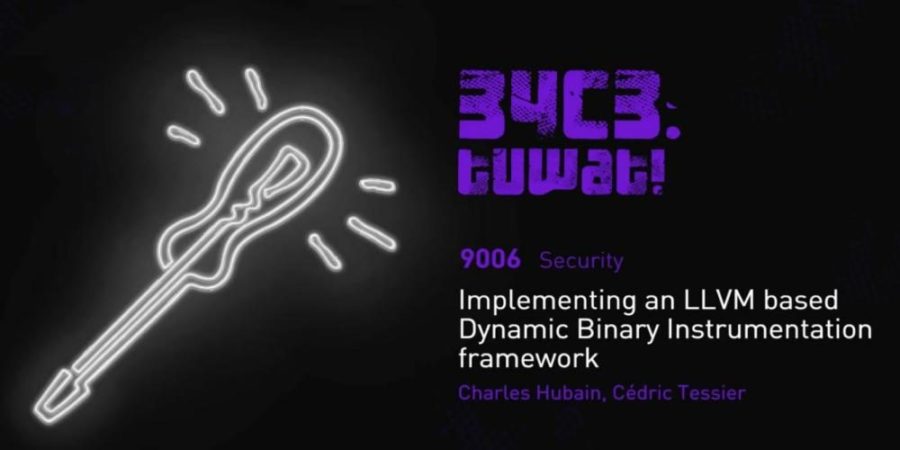
QuarkslaB Dynamic binary Instrumentation (QBDI) is a modular, cross-platform and cross-architecture DBI framework. It aims to support Linux, macOS, Android...
SDRtrunk is an integrated application for demodulating radio signals and decoding trunked radio network protocols and some related radio signal formats. The...
Microsoft is addressing unusual of the performance subdividing for fixing patches to relieve the Meltdown and Spectre vulnerabilities. Windows Chief Terry...