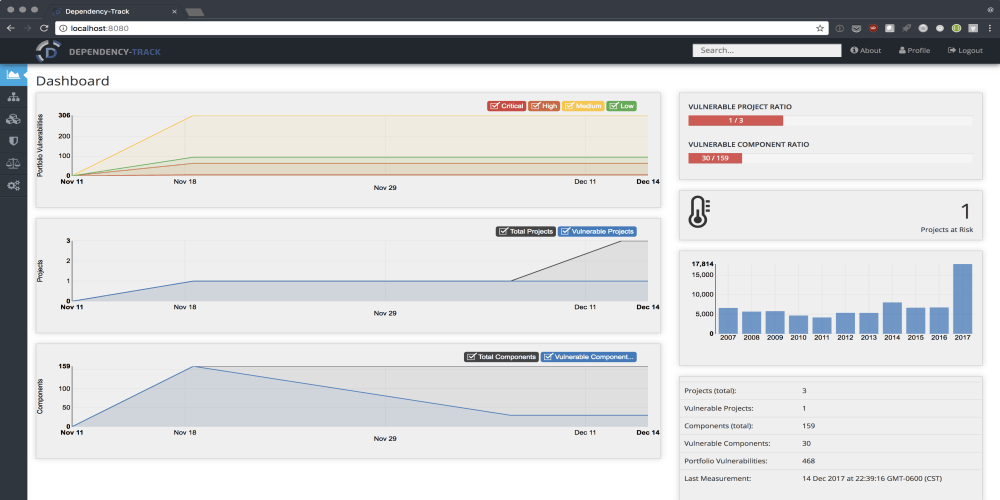
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
Search Results For - Node
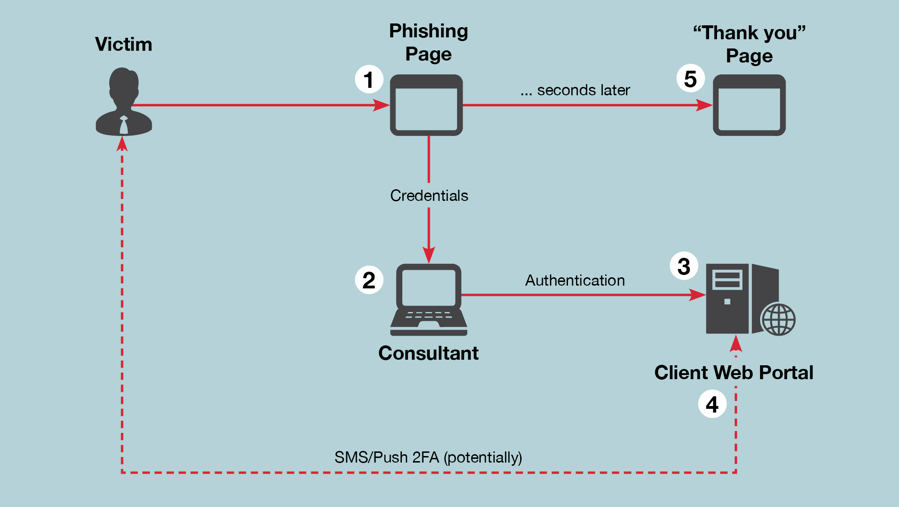
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
A modern BeEF inspired framework for the 21st century. Cross-platform clients => Web [in-browser] and Desktop [Electron]. Created from-scratch using pure...
Simple TCP reverse shell written in Go. It uses TLS to secure the communications, and provide a certificate public key fingerprint pinning feature, preventing...
The Nmap Scanner for Telco. With the current focus on telecom security, there used tools in day to day IT side penetration testing should be extended to...
BtleJuice is a complete framework to perform Man-in-the-Middle attacks on Bluetooth Smart devices (also known as Bluetooth Low Energy). It is composed of: an...
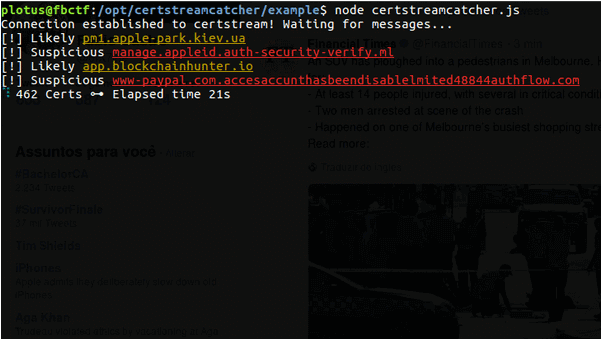
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
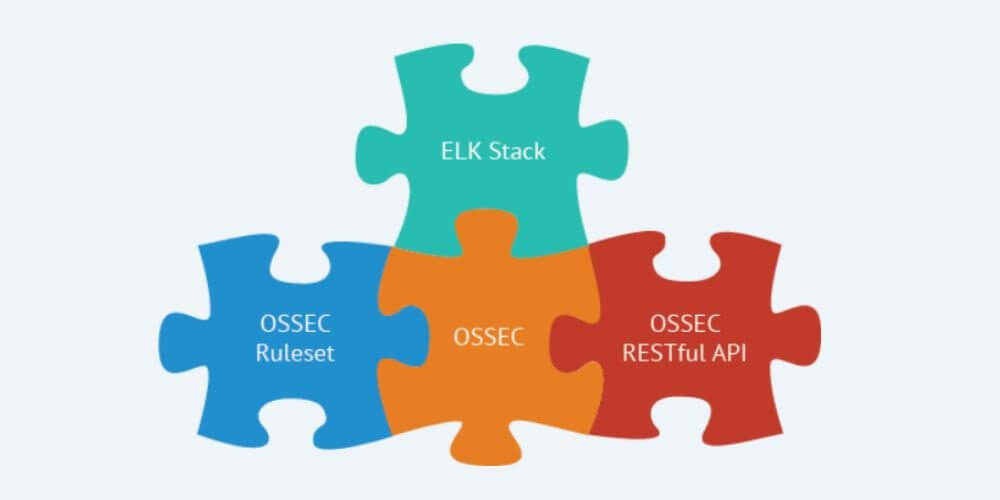
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...
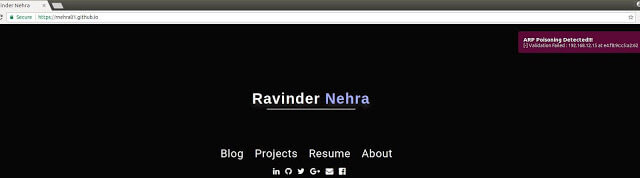
Security Tool to detect arp poisoning attacks. Features Uses a faster approach in detection of arp poisoning attacks compared to passive approaches Detects not...