Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
Search Results For - Node
Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...
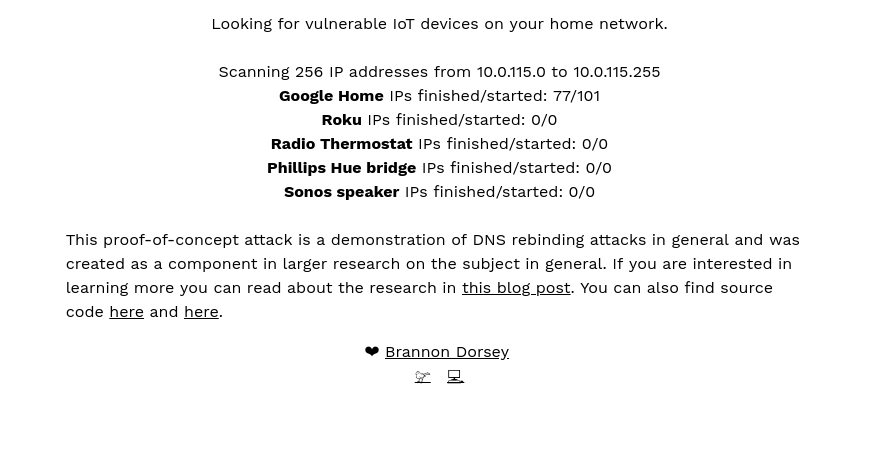
DNS Rebind Toolkit is a frontend JavaScript framework for developing DNS Rebinding exploits against vulnerable hosts and services on a local area...
The aerospace industry, comprising aviation and space flight, generates trillions of dollars every year. Countries compete for the latest and greatest...
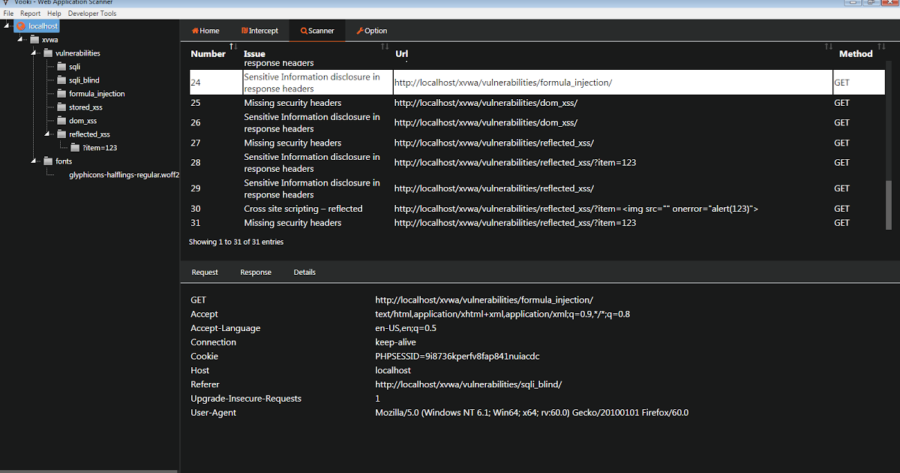
Vooki is a free web application vulnerability scanner. Vooki is a user-friendly tool that you can easily scan any web application and find the vulnerabilities...
pwnedOrNot is a python script which checks if the email account has been compromised in a data breach, if the email account is compromised it proceeds to find...
Author: Colin Harper If you’ve ever dealt in Bitcoin, you may have suffered through hour-long (or at worst, day-long) transaction times. It’s becoming...
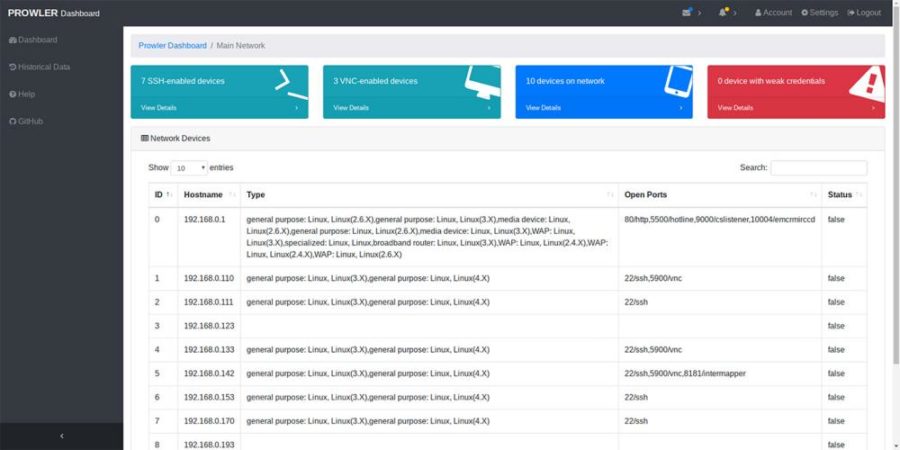
Prowler is a Network Vulnerability Scanner implemented on a Raspberry Pi Cluster, first developed during Singapore Infosec Community Hackathon – HackSmith v1.0...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...
Tool to check if a given IP is a node tor or an open proxy. Why? Sometimes all your throttles are not enough to stop brute force attacks or any kind of massive...