[sc name=”ad_1″] Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search...
Search Results For - Misconfiguration
[sc name=”ad_1″] This tool launches attack on k8s cluster from within. That means you already need to have an access with permission to deploy pods...
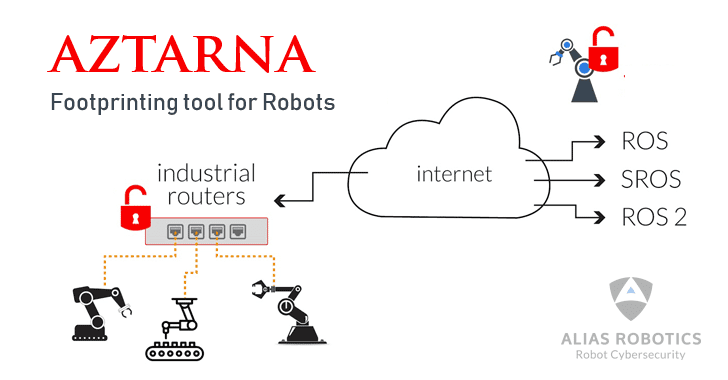
[sc name=”ad_1″] A team at a robot cybersecurity startup has released a free, open-source tool for information security professionals to help them...
[sc name=”ad_1″] A security researcher has discovered multiple one-click client-side vulnerabilities in the some of the world’s most popular...
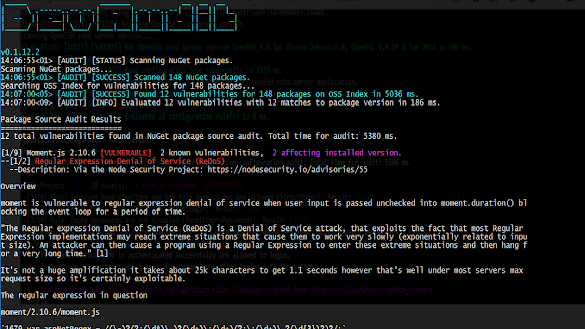
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...
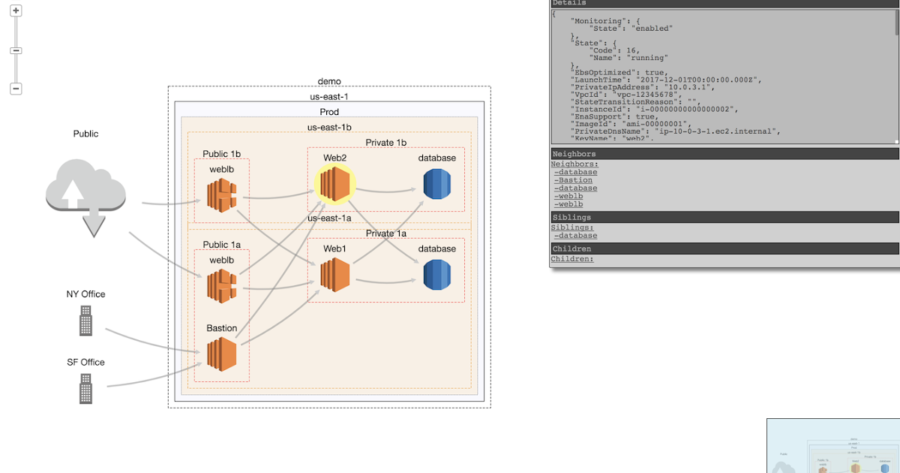
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your...
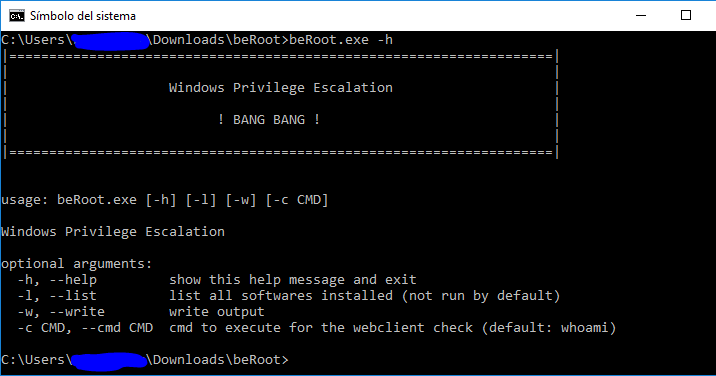
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...
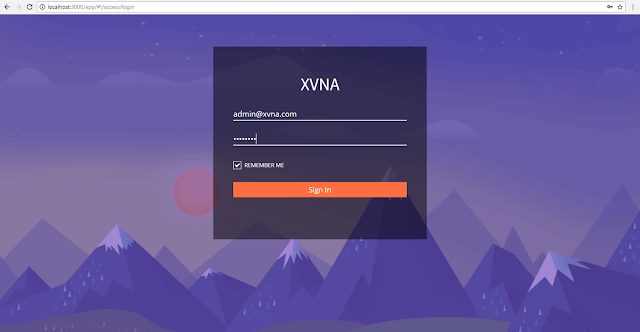
XVNA is an extreme vulnerable node application coded in Nodejs(Expressjs)/MongoDB that helps security enthusiasts to learn application security. it’s not...
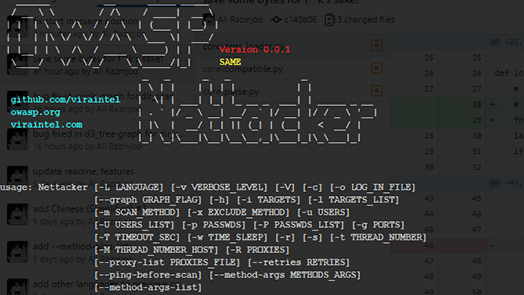
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
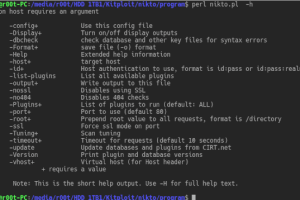
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially...