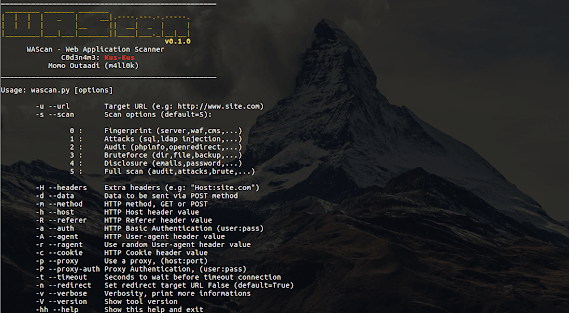
WAScan ((W)eb (A)pplication (Scan)ner) is a Open Source web application security scanner. It is designed to find various vulnerabilities using “black...
Search Results For - Management
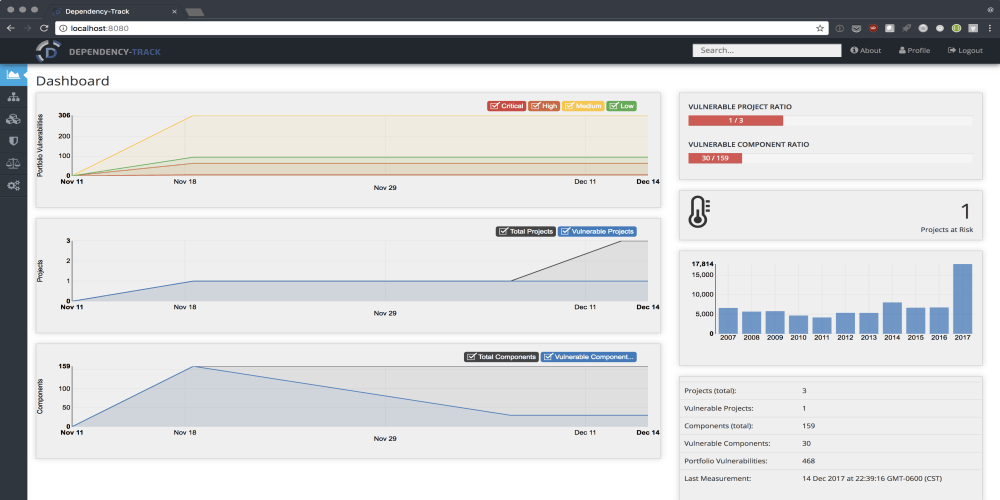
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
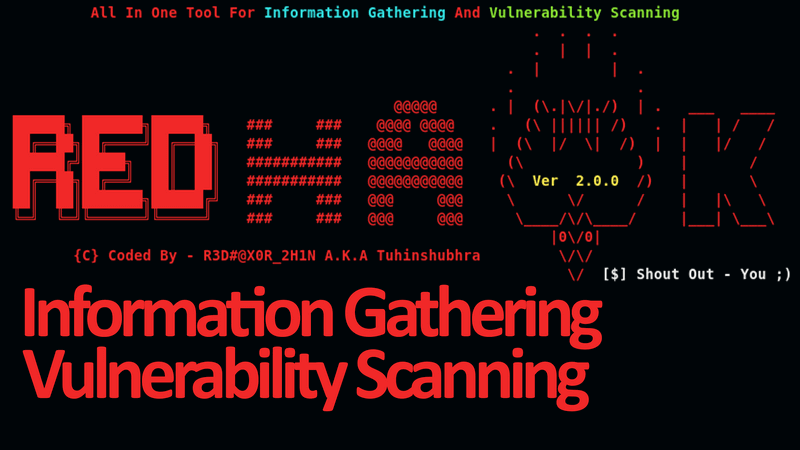
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP...
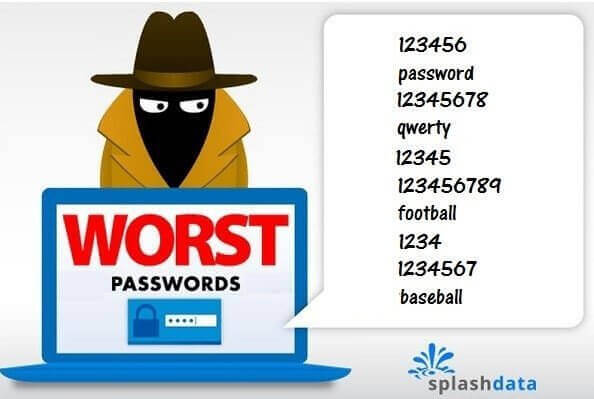
While becoming “123456” as your phrase is quite bad, the other phrases found on a list of Top 100 Worst Passwords of 2017 are just as distressing and...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
Youbit is a South Korean exchange that got hacked last week. As per reports, it is believed that around one-fifth of the clients’ holdings were stolen by...
Los Angeles natives Stefan Bogdanovich and Dakota Speas, represented by Wilshire Law Firm, this firm honed a lawsuit with the U.S. District Court for the...
The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to enable the main Genie DVR to communicate over...