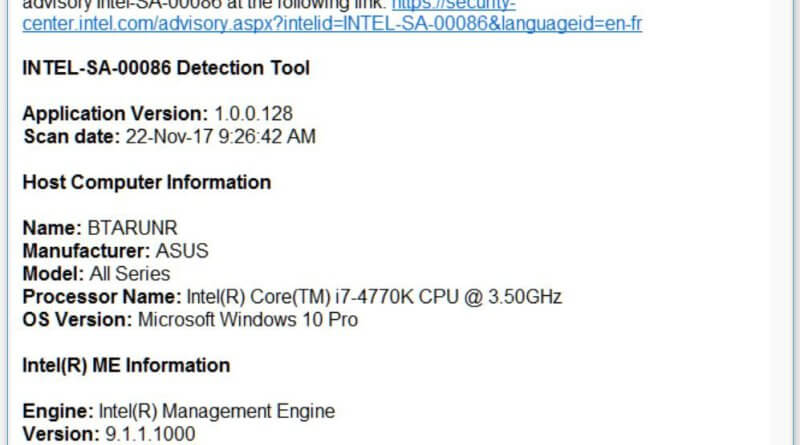
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to...
Search Results For - Mac OS X
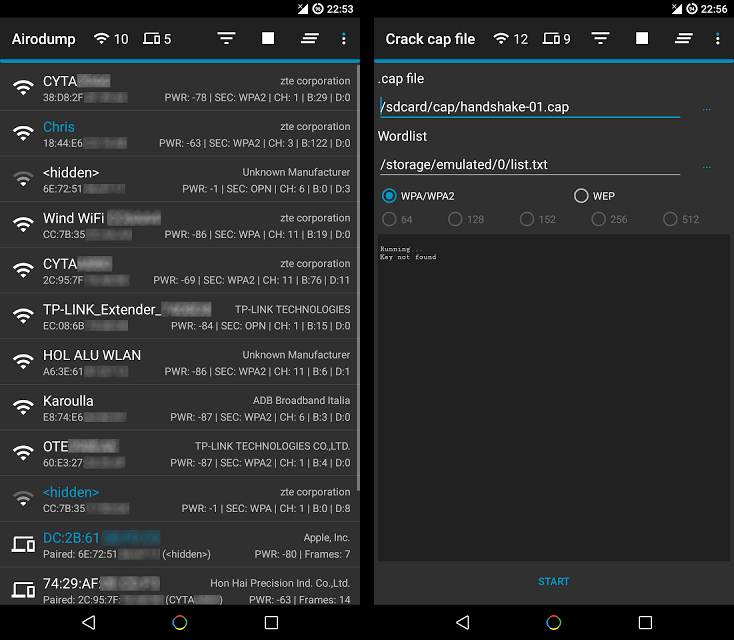
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...
ratched is a Man-in-the-Middle (MitM) proxy that specifically intercepts TLS connections. It is intended to be used in conjunction with the Linux iptables...
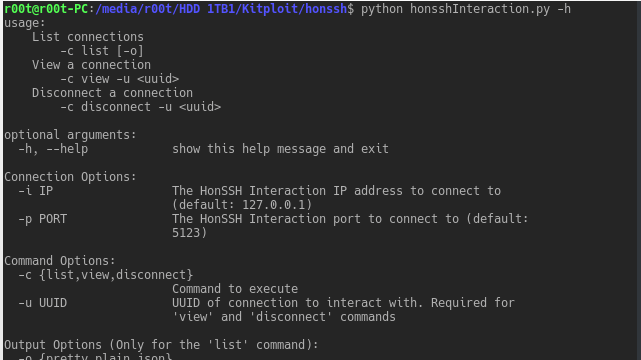
HonSSH is a high-interaction Honey Pot solution. HonSSH will sit between an attacker and a honey pot, creating two separate SSH connections between them...
Security Tool to detect arp poisoning attacks. Features Uses a faster approach in detection of arp poisoning attacks compared to passive approaches Detects not...
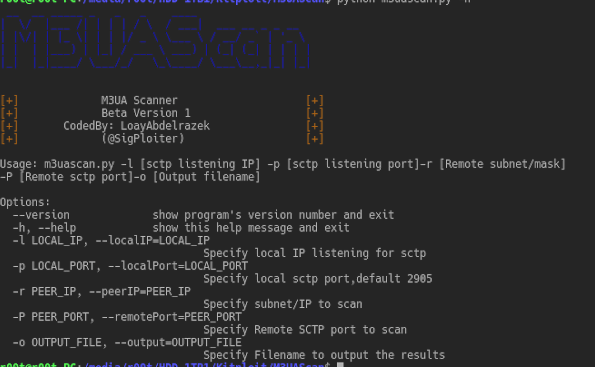
A Scanner for M3UA protocol to detect Sigtran supporting nodes M3UA stands for MTP Level 3 (MTP3) User Adaptation Layer as defined by the IETF SIGTRAN working...
The group, called Google You Owe Us, said in a declaration Thursday that it was the first case of its sort in the U.K. against a major tech business over the...
Amber is a proof of concept packer, it can pack regularly compiled PE files into reflective PE files that can be used as multi stage infection payloads. If you...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
Web Privacy Measurement is the observation of websites and serves to detect, characterize and quantify privacy-impacting behaviors. Applications of Web Privacy...