Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
Search Results For - Mac OS X
Magic Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber’s powershell attacks...
Hardentools is a collection of simple utilities designed to disable a number of “features” exposed by operating systems (Microsoft Windows, for now), and...
bettercap is the Swiss army knife for network attacks and monitoring. How to Install A precompiled version is available for each release, alternatively you can...
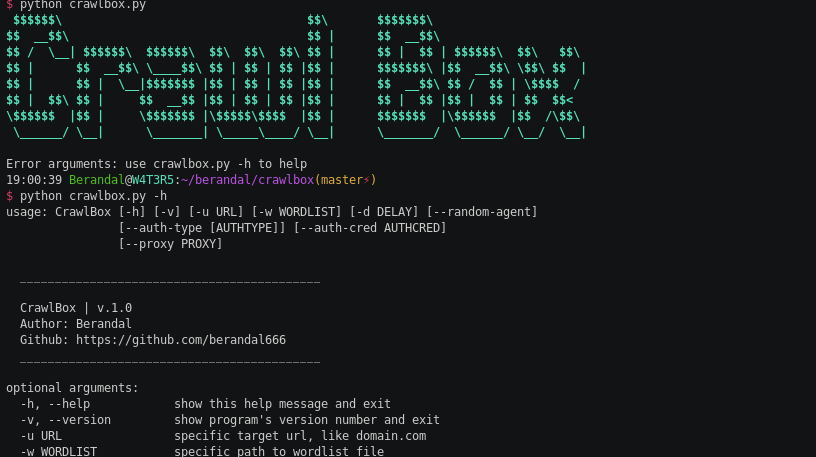
Easy way to brute-force web directory. Operating Systems Tested: MacOSX Kali Linux Usage: python crawlbox.py [-h] [-v] [-w WORDLIST] url positional arguments:...
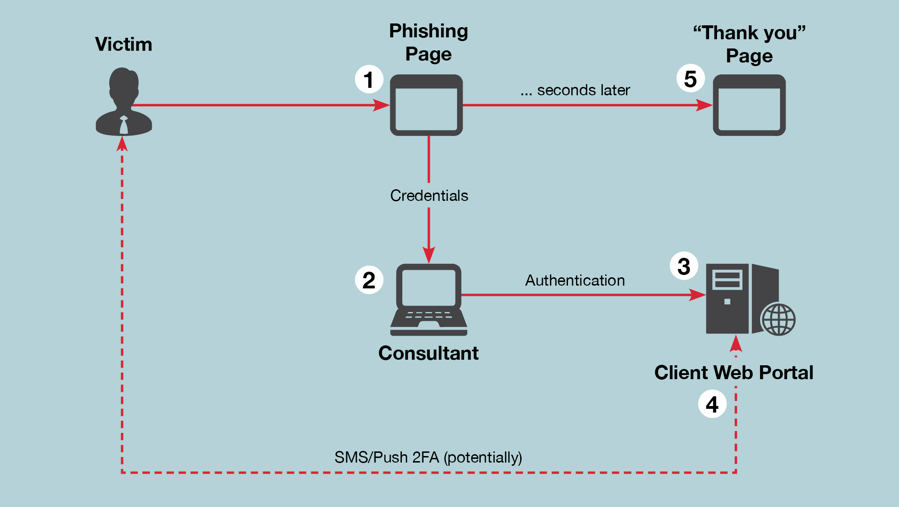
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
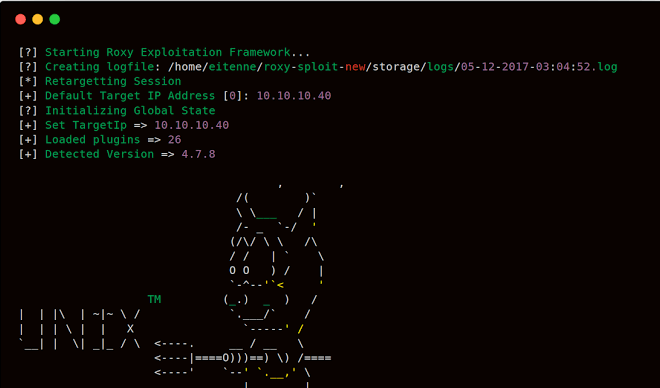
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...
Kali Linux 2018.1 the first release of 2018, this fine release contains all updated packages and bug fixes since our 2017.3 release last November. This release...
Grouper is a slightly wobbly PowerShell module designed for pentesters and redteamers (although probably also useful for sysadmins) which sifts through the...
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...