Monitor illegal wireless network activities. Similar SSID broadcasts Same SSID broadcasts Calculates unencrypted wireless networks density Watches SSID...
Search Results For - Logs
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
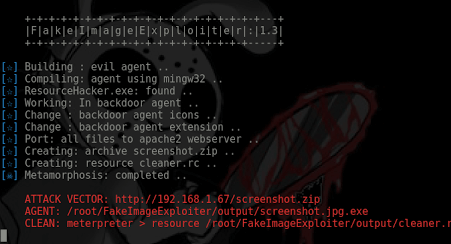
This module takes one existing image.jpg and one payload.ps1 (input by user) and builds a new payload (agent.jpg.exe) that if executed it will trigger the...
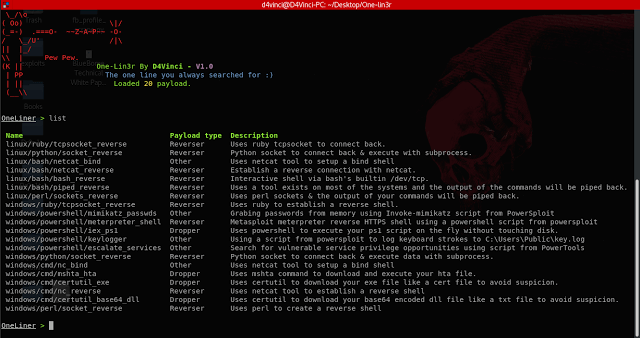
One-Lin3r is simple and light-weight framework inspired by the web-delivery module in Metasploit. It consists of various one-liners that aids in penetration...
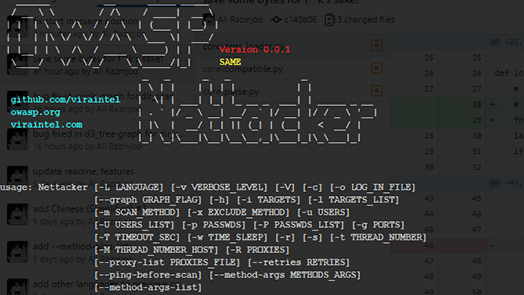
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are...
Millions of people have become victims of a FakeApp that is using new tricks to cheat Uber users around the world. Security researchers from Symantec...
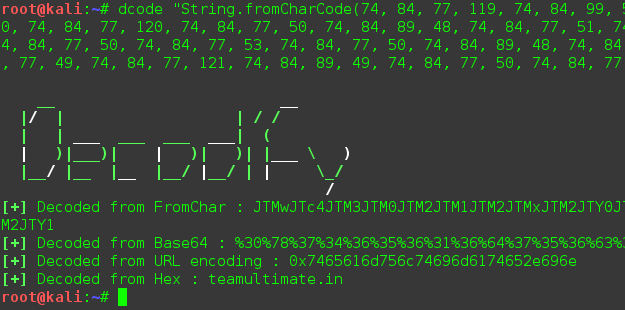
Decodify can detect and decode encoded strings, recursively. Its currently in beta phase. Lets take this string : teamultimate.in and encode it with Hex, URL...
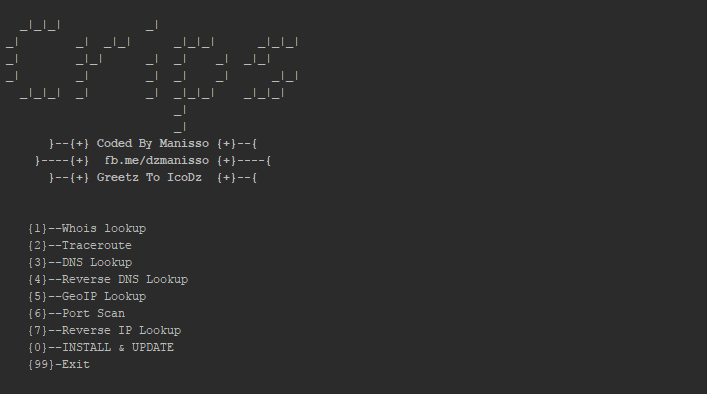
This Tools is a collection of online IP Tools that can be used to quickly get information about IP Address’s, Web Pages and DNS records. Menu Whois...
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...