Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to...
Search Results For - Logs
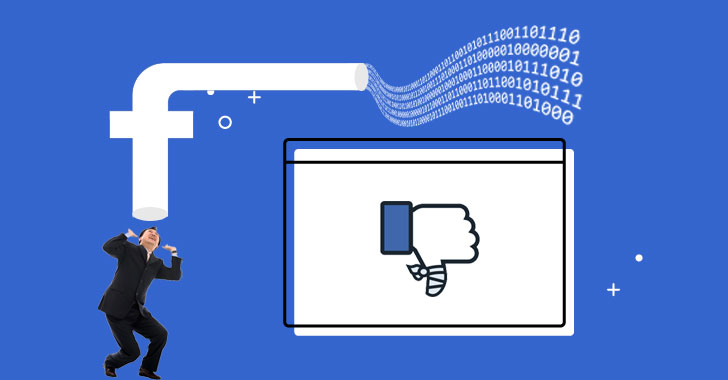
Late last month Facebook announced its worst-ever security breach that allowed an unknown group of hackers to steal secret access tokens for millions of...
Yes, it is official. The massively popular battle royale video game from Epic Games, Fortnite: Battle Royale is finally available for Android devices. Epic...
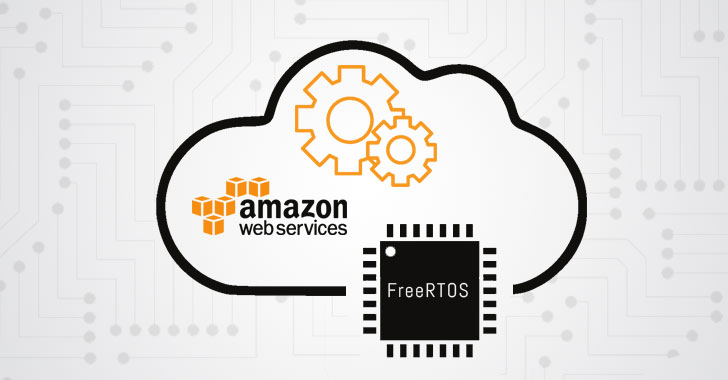
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
Cybersecurity researchers have revealed an unpatched logical flaw in Microsoft Office 2016 and older versions that could allow an attacker to embed malicious...
Microsoft Windows built-in anti-malware tool, Windows Defender, has become the very first antivirus software to have the ability to run inside a sandbox...
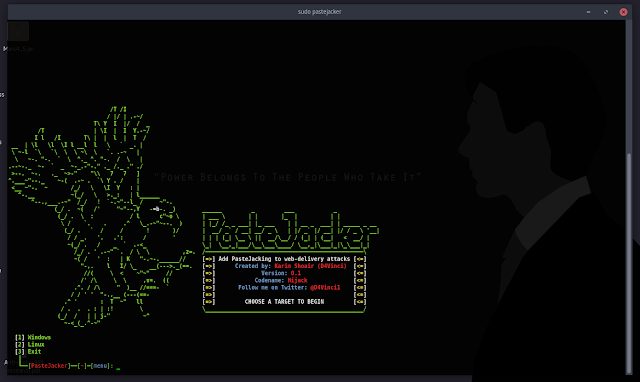
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this...
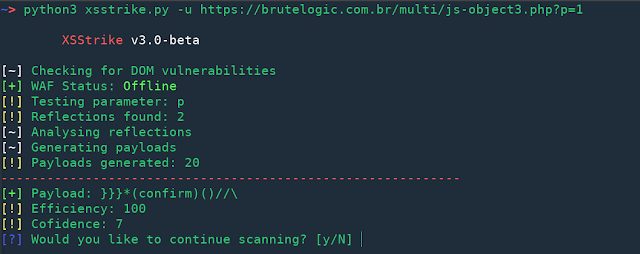
Why XSStrike? Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared...
Nubia is a lightweight framework for building command-line applications with Python. It was originally designed for the “logdevice interactive shell (aka...
An Indian security researcher has discovered a highly critical flaw in X.Org Server package that impacts OpenBSD and most Linux distributions, including...