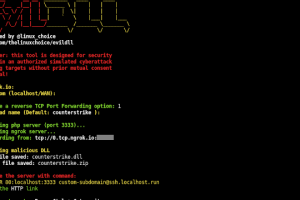
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Malicious DLL (Win Reverse Shell) generator for DLL Hijacking Features:...
Search Results For - Logs
[sc name=”ad_1″] Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right...
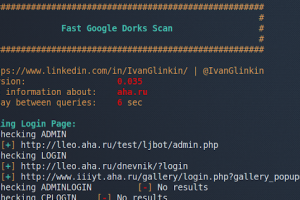
[sc name=”ad_1″] A script to enumerate web-sites using Google dorks. Usage example: ./FGDS.sh megacorp.one Version: 0.035, June 07, 2020 Features:...
[sc name=”ad_1″] Chrome extension for Instant access to your bug bounty submission dashboard of various platforms + publicly disclosed reports +...
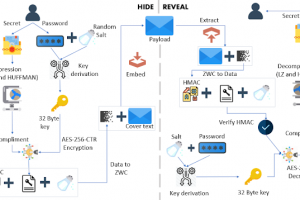
[sc name=”ad_1″] StegCloak is a pure JavaScript steganography module designed in functional programming style, to hide secrets inside text by...
[sc name=”ad_1″] RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without...
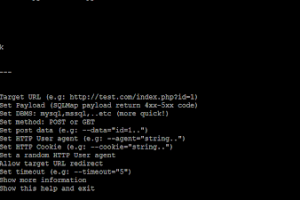
[sc name=”ad_1″] Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code...
[sc name=”ad_1″] URLCrazy is an OSINT tool to generate and test domain typos or variations to detect or perform typo squatting, URL hijacking...
[sc name=”ad_1″] Impost3r is a tool that aim to steal many kinds of linux passwords(including ssh,su,sudo) written by C. Attackers can use Impost3r...
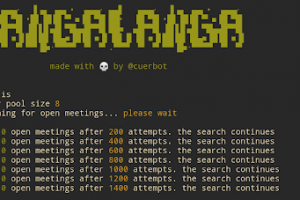
[sc name=”ad_1″] Zoom Conference scanner. This scanner will check for a random meeting id and return information if available. Usage This are all...