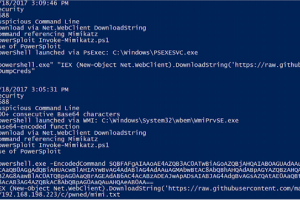
[sc name=”ad_1″] DeepBlueCLI – a PowerShell Module for Threat Hunting via Windows Event Logs Eric Conrad, Backshore Communications, LLC...
Search Results For - Logs
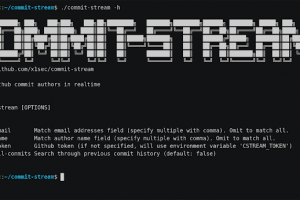
[sc name=”ad_1″] commit-stream drinks commit logs from the Github event firehose exposing the author details (name and email address) associated...
[sc name=”ad_1″] A California-based Voice-Over-IP (VoIP) services provider VOIPO has accidentally left tens of gigabytes of its customer data...
Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
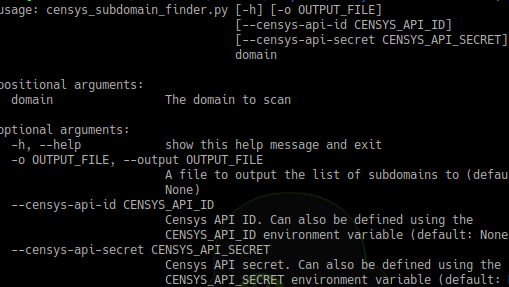
This is a tool to enumerate subdomains using the Certificate Transparency logs stored by Censys. It should return any subdomain who has ever been issued a SSL...
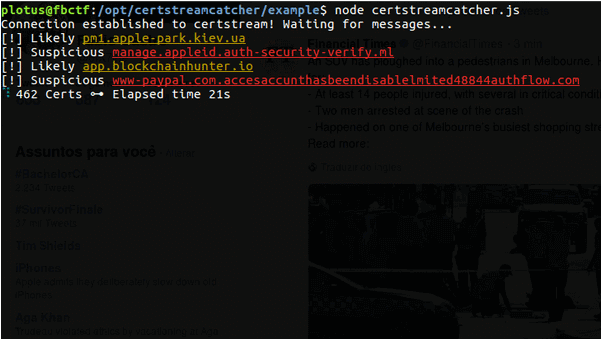
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
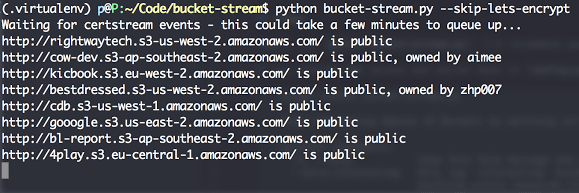
Some quick tips if you use S3 buckets: Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com. Set appropriate permissions and...
Today, 9 November 2017, WikiLeaks publishes the source code and development logs to Hive, a major component of the CIA infrastructure to control its malware...
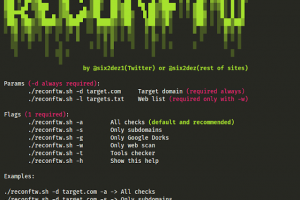
[sc name=”ad_1″] This is a simple script intended to perform a full recon on an objective with multiple subdomains tl;dr Requires Go Run ./install...
[sc name=”ad_1″] HosTaGe is a lightweight, low-interaction, portable, and generic honeypot for mobile devices that aims on the detection of...