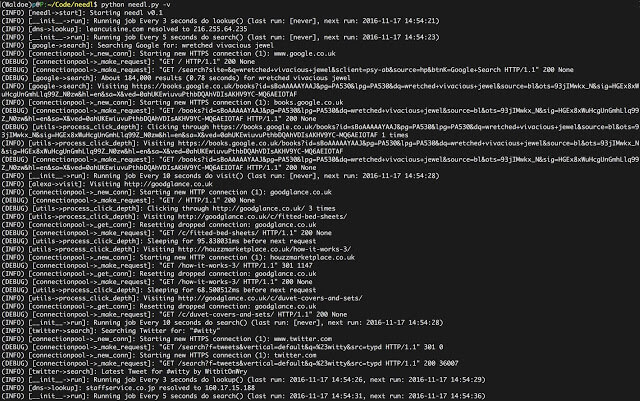
Take back your privacy. Lose yourself in the haystack. Your ISP is most likely tracking your browsing habits and selling them to marketing agencies (albeit...
Search Results For - Linux
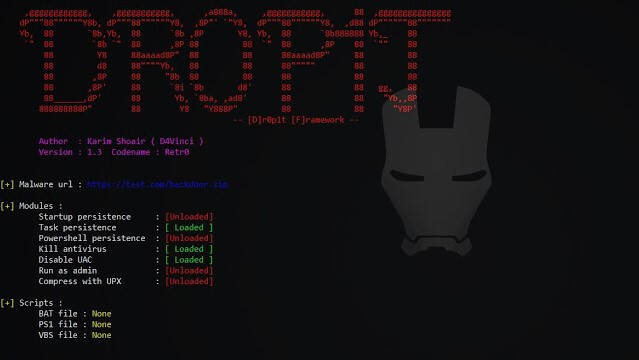
Have you ever heard about trojan droppers ? In short dropper is type of malware that downloads other malwares and Dr0p1t gives you the chance to create a...
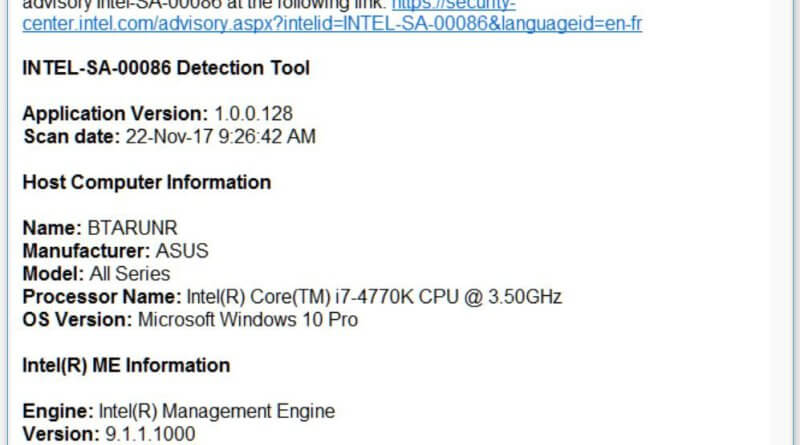
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to...
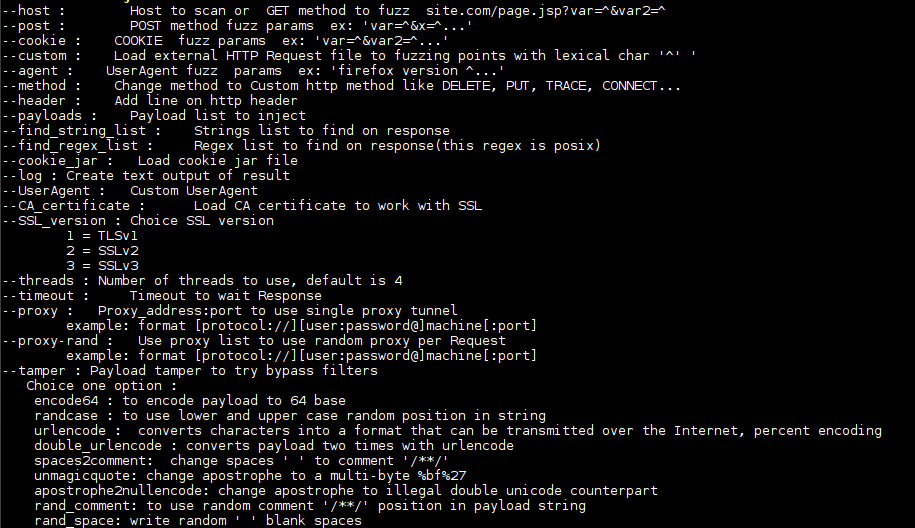
Web security tool to make fuzzing at HTTP inputs, made in C with libCurl. 0d1n is a tool for automating customized attacks against web applications. You can...
ratched is a Man-in-the-Middle (MitM) proxy that specifically intercepts TLS connections. It is intended to be used in conjunction with the Linux iptables...
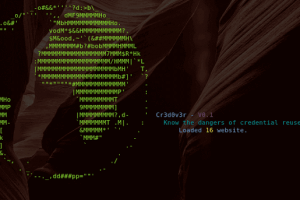
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
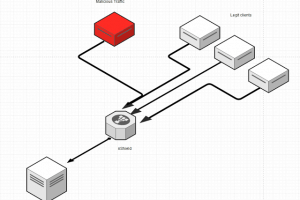
An Easy and Simple Anti-DDoS solution for VPS,Dedicated Servers and IoT devices based on iptables. Requirements Linux System with python, iptables Nginx (Will...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
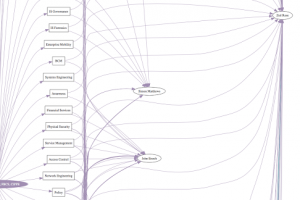
An OSINT tool that allows you to draw out relationships between people on LinkedIn via endorsements/skills. Check out the example (digraph), which is based on...
A user-friendly Web interface to share an hashcat cracking box among multiple users with some pre-defined options. Outline This Web application can be used to...