[sc name=”ad_1″] Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk...
Search Results For - Leaks
[sc name=”ad_1″] Security Tool for Reconnaissance and Information Gathering on a website. (python 2.x & 3.x) This script use...
[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...
[sc name=”ad_1″] A Proof-of-Concept bind shell using the Fax service and a DLL hijack based on Ualapi.dll. See our writeup at: How to use Build...
[sc name=”ad_1″] Working and learning have gone remote, and we have to come to terms with this new reality. Nowadays, several organizations allow...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
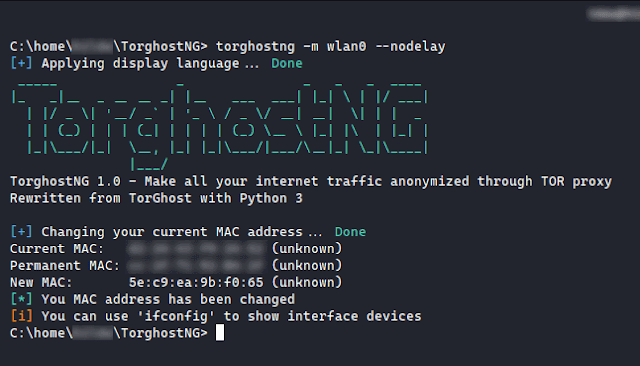
[sc name=”ad_1″] TorghostNG is a tool that make all your internet traffic anonymized through Tor network. Rewritten from TorGhost with Python 3...
[sc name=”ad_1″] gitGraber is a tool developed in Python3 to monitor GitHub to search and find sensitive data for different online services such...
[sc name=”ad_1″] The United States’ National Security Agency (NSA) today finally released GHIDRA version 9.0 for free, the agency’s home...
[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high...