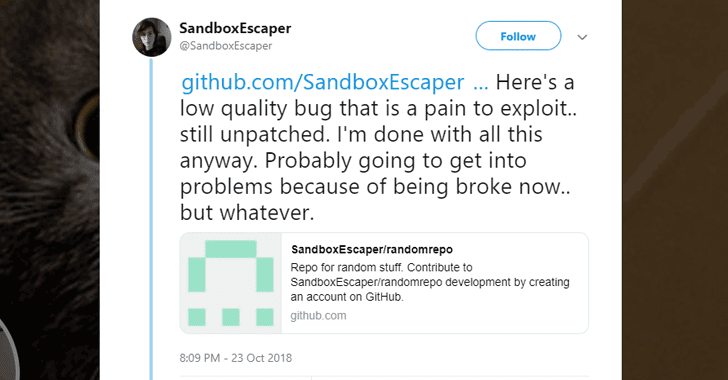
A security researcher with Twitter alias SandboxEscaper—who two months ago publicly dropped a zero-day exploit for Microsoft Windows Task Scheduler—has...
Search Results For - Leaked
State-of-the-art password guessing tools, such as HashCat and John the Ripper (JTR), enable users to check billions of passwords per second against password...
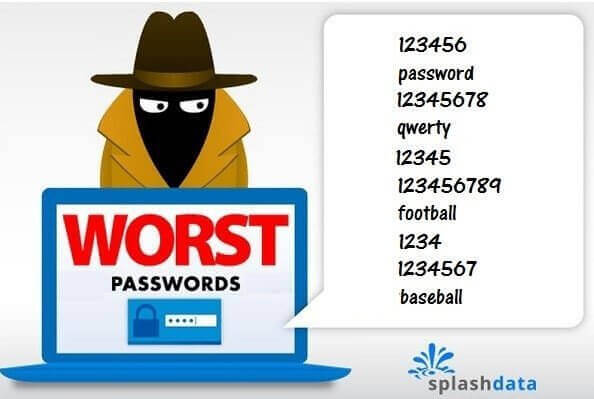
While becoming “123456” as your phrase is quite bad, the other phrases found on a list of Top 100 Worst Passwords of 2017 are just as distressing and...
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
Tweep is an advanced Twitter scraping tool written in python that allows for scraping Tweets and pictures from Twitter profiles without using Twitter’s...
The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
An unknown hacker has hijacked Coinhive’s DNS server and modified the legitimate Coinhive JavaScript in-browser miner with a malicious one that mined Monero...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...