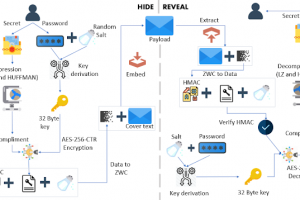
[sc name=”ad_1″] StegCloak is a pure JavaScript steganography module designed in functional programming style, to hide secrets inside text by...
Search Results For - Invisible
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
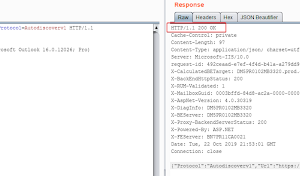
[sc name=”ad_1″] A script that can see if an email address is valid in Office365. This does not perform any login attempts, is unthrottled, and is...
[sc name=”ad_1″] HyperDbg is designed with a focus on using modern hardware technologies to provide new features to the reverse engineering world...
[sc name=”ad_1″] A Cross Platform Remote Administration tool written in Go using Tor as its transport mechanism currently supporting Windows...
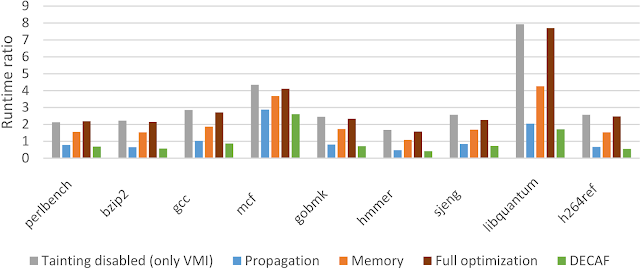
[sc name=”ad_1″] DECAF++, the new version of DECAF, taint analysis is around 2X faster making it the fastest, to the best of our knowledge, whole...
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] It’s 2019, and just opening an innocent looking office document file on your system can still allow hackers to compromise...
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...