[sc name=”ad_1″] A collection of cool tools used by Mobile hackers. Happy hacking , Happy bug-hunting Weapons OS Type Name Description All Analysis...
Search Results For - Inject Code
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] This cli is for pentesters, CTF players, or dev. You can modify your jwt, sign, inject ,etc… Check Documentation for more...
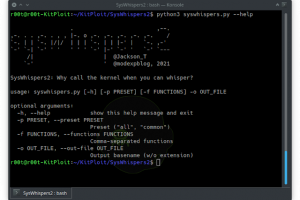
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
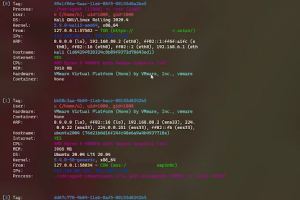
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
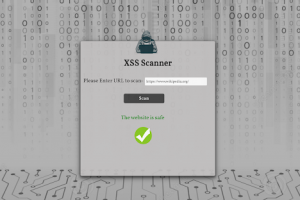
[sc name=”ad_1″] Cross-Site Scripting (XSS) is one of the most well known web application vulnerabilities. It even has a dedicated chapter in the...
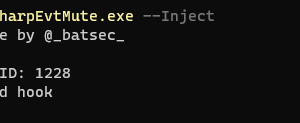
[sc name=”ad_1″] This is a tool that allows you to offensively use YARA to apply a filter to the events being reported by windows event logging...
[sc name=”ad_1″] 0d1n is a tool for automating customized attacks against web applications. This tool is very faster because uses thread pool and C...
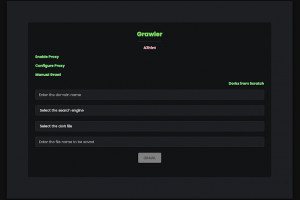
[sc name=”ad_1″] Grawler is a tool written in PHP which comes with a web interface that automates the task of using google dorks, scrapes the...
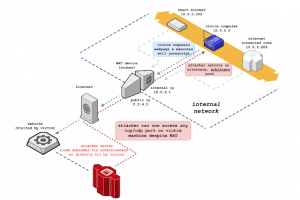
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...