ElasticIntel is serverless, low cost, threat intel aggregation for enterprise or personal use, backed by ElasticSearch. It is an alternative to expensive...
Search Results For - Information
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
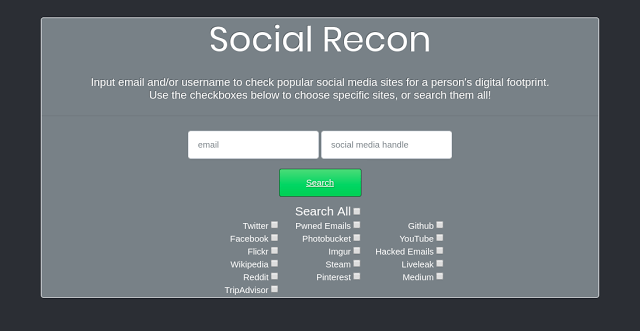
This application locates and compiles information about online personalities, given a username and/or email address. Use this to investigate your own online...
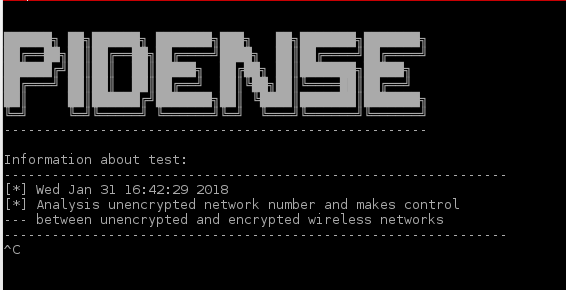
Monitor illegal wireless network activities. Similar SSID broadcasts Same SSID broadcasts Calculates unencrypted wireless networks density Watches SSID...
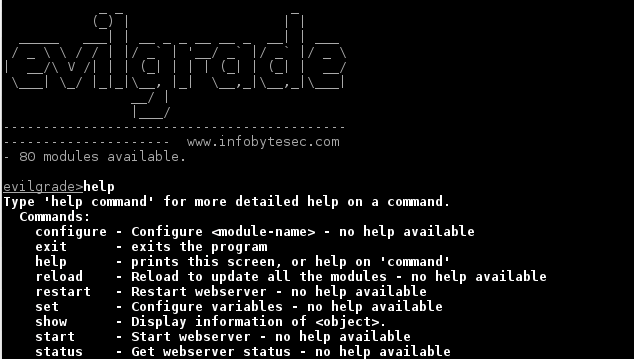
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
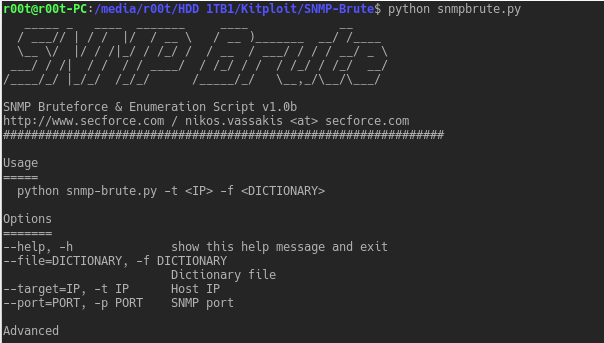
SNMP brute force, enumeration, CISCO config downloader and password cracking script. Listens for any responses to the brute force community strings...
Spectre & Meltdown Checker A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs...
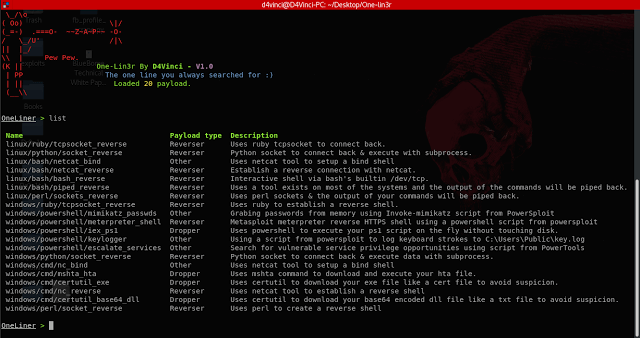
One-Lin3r is simple and light-weight framework inspired by the web-delivery module in Metasploit. It consists of various one-liners that aids in penetration...
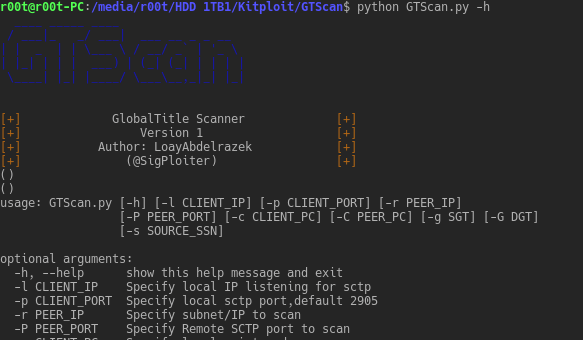
The Nmap Scanner for Telco. With the current focus on telecom security, there used tools in day to day IT side penetration testing should be extended to...