[sc name=”ad_1″] For the most up-to-date information on Anchore Engine, Anchore CLI, and other Anchore software, please refer to the Anchore...
Search Results For - Information
[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
[sc name=”ad_1″] There are better ways than managing vulnerabilities with spreadsheets, especially when you are working with several tools. We know...
[sc name=”ad_1″] Bug Bounty Recon (bbrecon) is a free Recon-as-a-Service for bug bounty hunters and security researchers. The API aims to provide a...
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
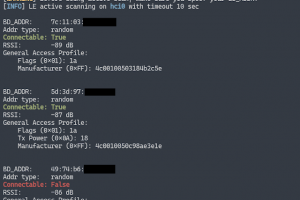
[sc name=”ad_1″] Bluescan is a open source project by Sourcell Xu from DBAPP Security HatLab. Anyone may redistribute copies of bluescan to anyone...
[sc name=”ad_1″] A multi-threaded AWS inventory collection tool. The creators of this tool have a recurring need to be able to efficiently collect...