[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
Search Results For - Hijacking
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to...
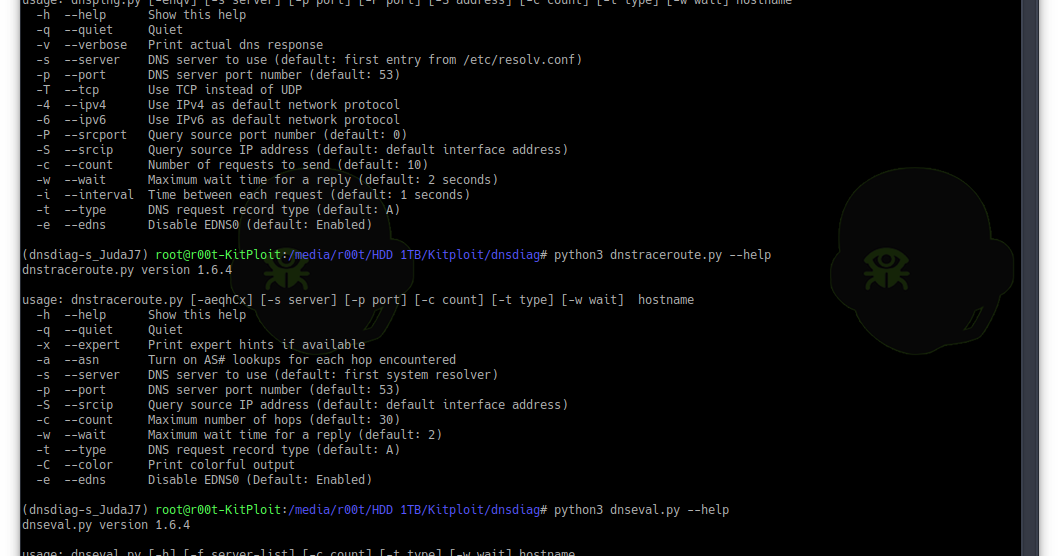
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...
Sn1per Community Edition is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Sn1per...
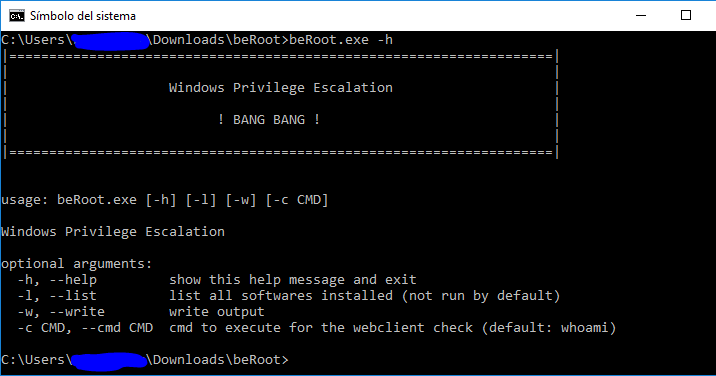
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...
Sn1per is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Features: Automatically collects basic...
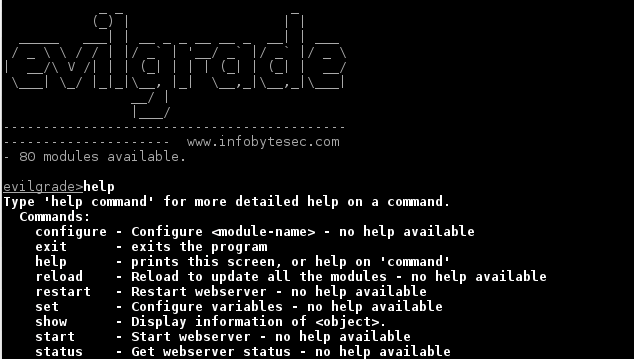
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...