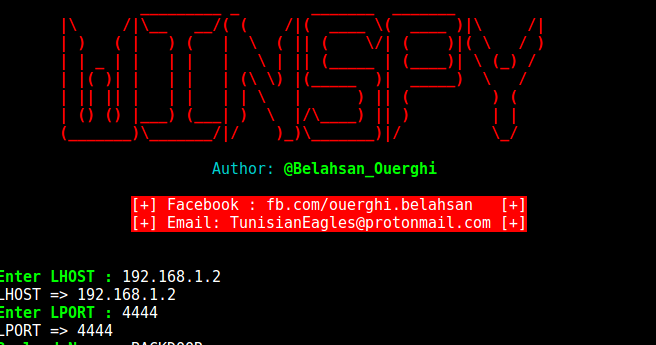
WinSpy: Windows Reverse Shell Backdoor Creator With ip poisener. Dependencies 1 – metasploit-framework 2 – xterm 3 – apache2 4 –...
Search Results For - Hidden
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
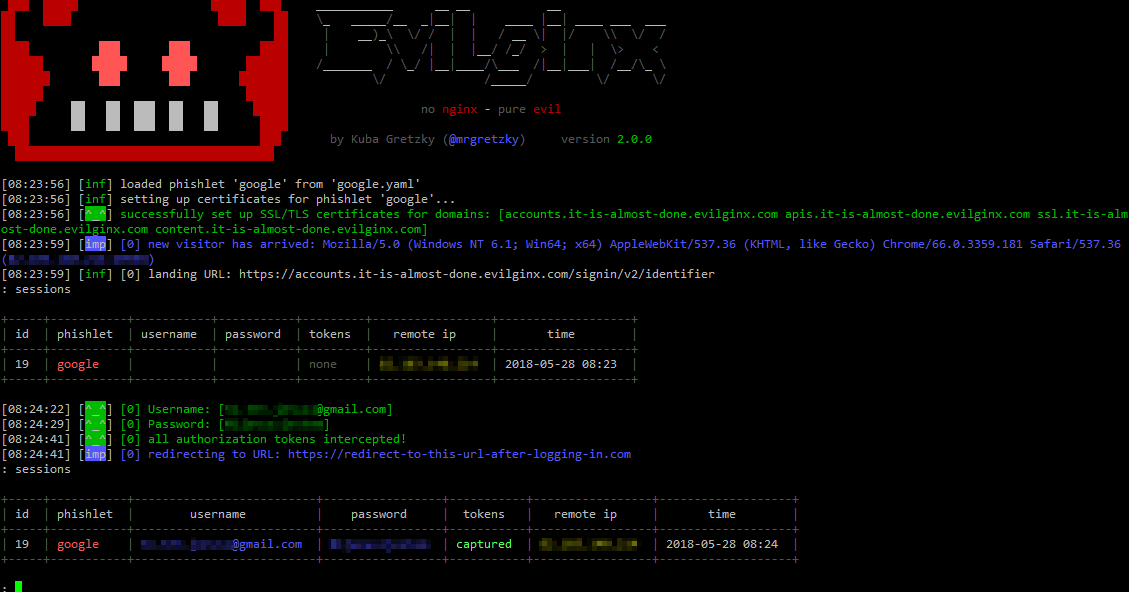
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor...
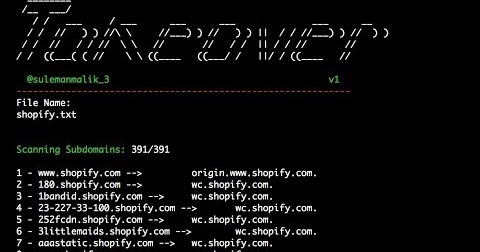
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...
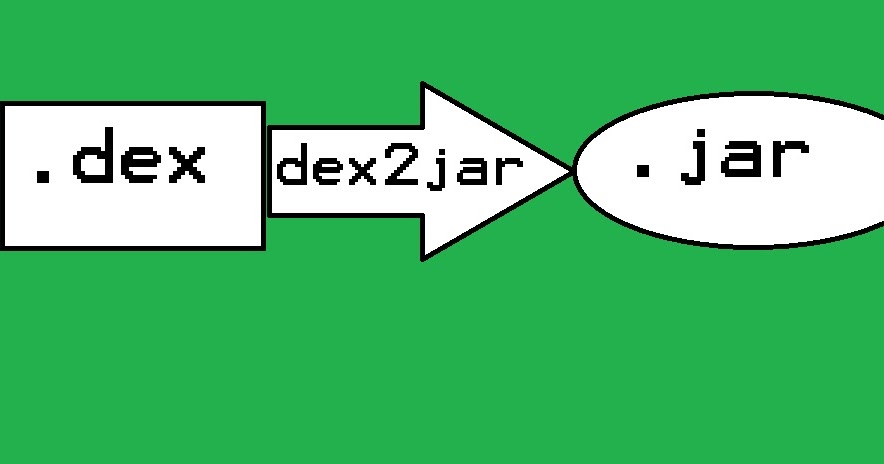
dex2jar Tools to work with android .dex and java .class files dex-reader/writer: Read/write the Dalvik Executable (.dex) file. It has a light weight API...
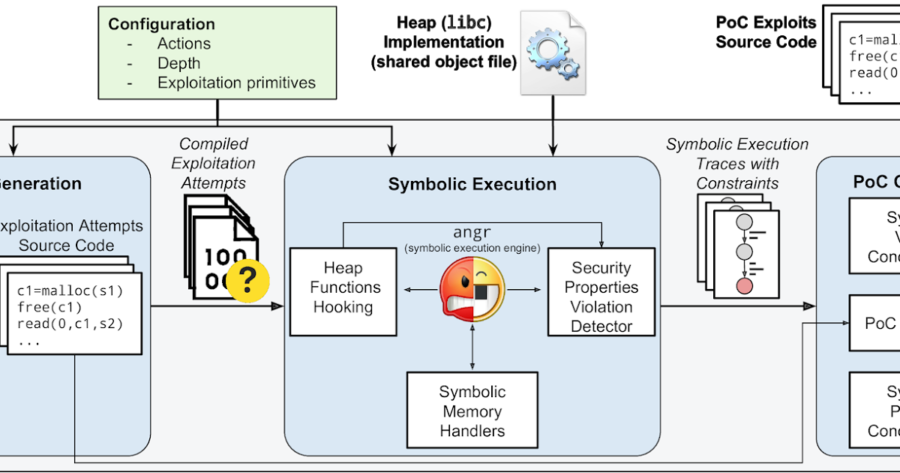
HeapHopper is a bounded model checking framework for Heap-implementations. Setup sudo apt update && sudo apt install build-essential python-dev...
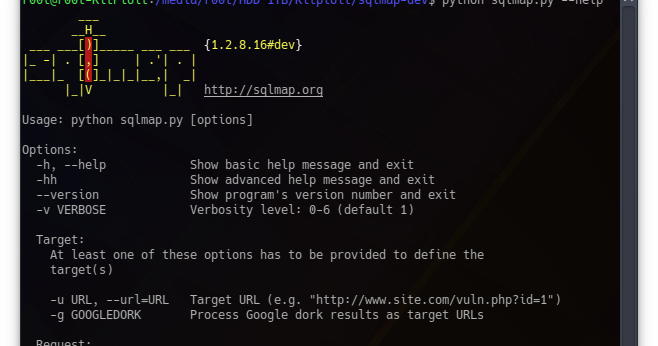
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
Ducky Exploit is python framework which helps as to code Digispark as Rubber Ducky. This script has been tested on Kali Linux 18.2 Ubuntu 18.04 Windows Works...
Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website on Apache Server...
Weevely is a web shell designed for post-exploitation purposes that can be extended over the network at runtime. Upload weevely PHP agent to a target web...