[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...
Search Results For - Hidden
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
ACHE is a focused web crawler. It collects web pages that satisfy some specific criteria, e.g., pages that belong to a given domain or that contain a user...
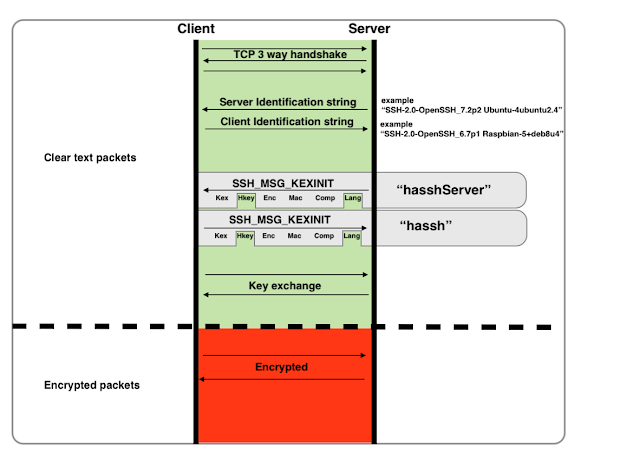
“HASSH” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be...
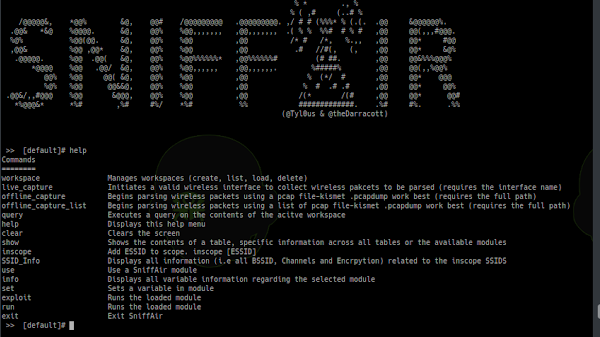
SniffAir is an open-source wireless security framework which provides the ability to easily parse passively collected wireless data as well as launch...
Welcome to our fourth and final release of 2018, Kali Linux 2018.4, which is available for immediate download. This release brings kernel up to version 4.18...
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this...
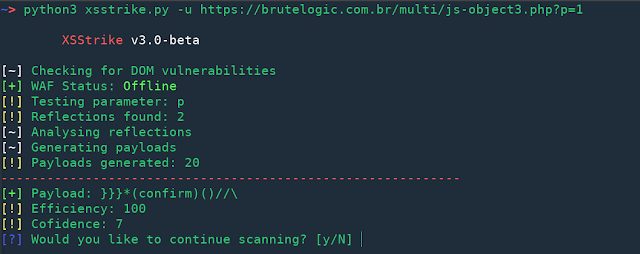
Why XSStrike? Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared...
Bashark aids pentesters and security researchers during the post-exploitation phase of security audits. Usage To launch Bashark on compromised host, simply...
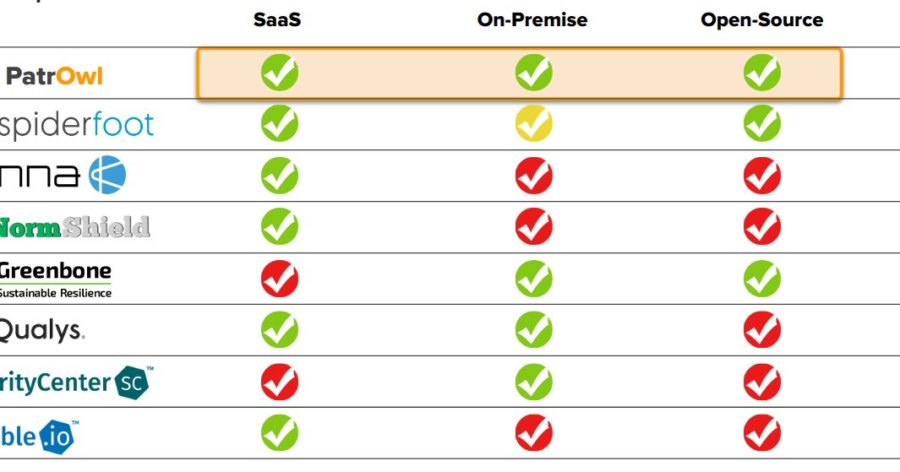
PatrOwl is a scalable, free and open-source solution for orchestrating Security Operations. PatrowlManager is the Front-end application for managing the...