The term “location services” oftentimes points to exact GPS data for app usage, such as Google Maps discovering your best commute route, or Uber figuring...
Search Results For - Hackers
The firm looked at nearly 70 million emails sent during October from 5,000 different .gov origin domains preserved by Proofpoint, the company’s VP of Email...
When ironed about how Yahoo failed to realize that 3 billion accounts and not 500 million as first proclaimed were endangered in what was later revealed to be...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
The Google Play store has made headlines recently when cyber criminals were able to hack in and post a fake WhatsApp messenger update for download. More than a...
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
Striker is an offensive information and vulnerability scanner. Features Just supply a domain name to Striker and it will automatically do the following for...
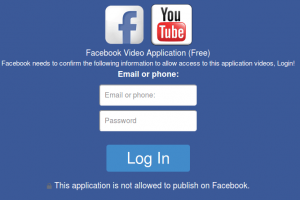
A new Facebook spam campaign has been detected by F-Secure security researchers, the campaign attracting users to phishing pages that attempt to fool users...
The flaw was discovered by researchers from Check Point in the user authentication method between the SmartThinQ portable app and LG’s back-end platform. This...