Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to...
Search Results For - Exploiting
Microsoft Windows built-in anti-malware tool, Windows Defender, has become the very first antivirus software to have the ability to run inside a sandbox...
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
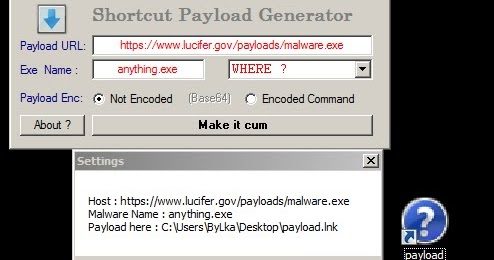
Making FUD Shortcut (.lnk) payloads with LNK-KISSER to remote execute malicious code. Shortcut-Payload-Generator Exploiting Powershell to make ShortCut...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
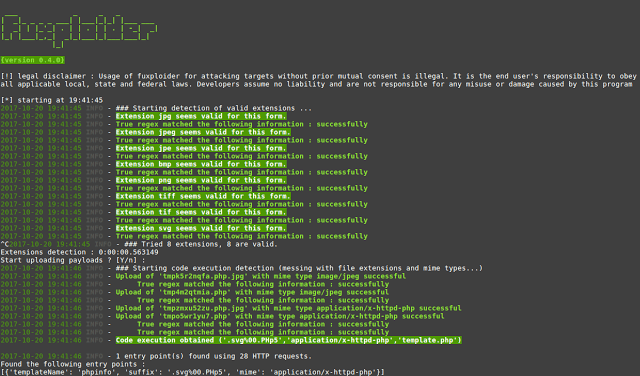
fuxploider is an open source penetration testing tool that automates the process of detecting and exploiting file upload forms flaws. This tool is able to...
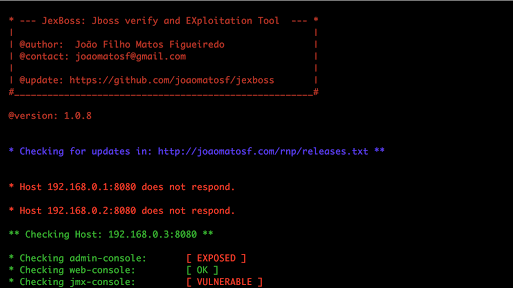
JexBoss is a tool for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms, Frameworks, Applications, etc. Requirements...
The U.S. federal officials have arrested two hackers who have pleaded guilty to computer-crimes charges for creating and distributing Mirai botnet that...
Palihapitiya’s judgments were directed not only at Facebook but the broader online ecosystem. “The short-term, dopamine-driven feedback circles we’ve produced...