[sc name=”ad_1″] If the connectivity and security of your organization rely on Cisco RV320 or RV325 Dual Gigabit WAN VPN routers, then you need to...
Search Results For - Exploiting
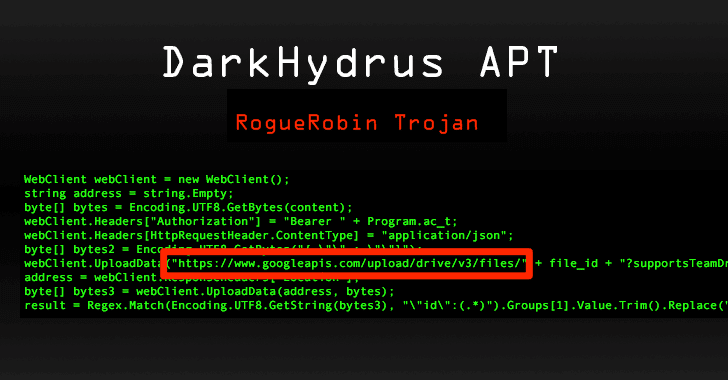
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...
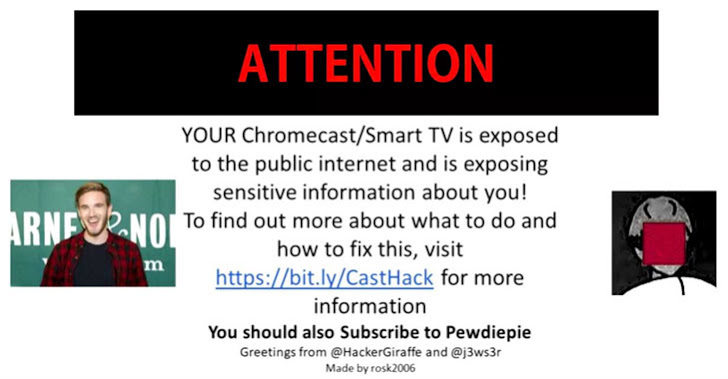
[sc name=”ad_1″] A group of hackers has hijacked tens of thousands of Google’s Chromecast streaming dongles, Google Home smart speakers and...
[sc name=”ad_1″] Microsoft today issued an out-of-band security update to patch a critical zero-day vulnerability in Internet Explorer (IE) Web...
[sc name=”ad_1″] Here we have great news for all bug bounty hunters. Now you can get paid up to $40,000 for finding and responsibly reporting...
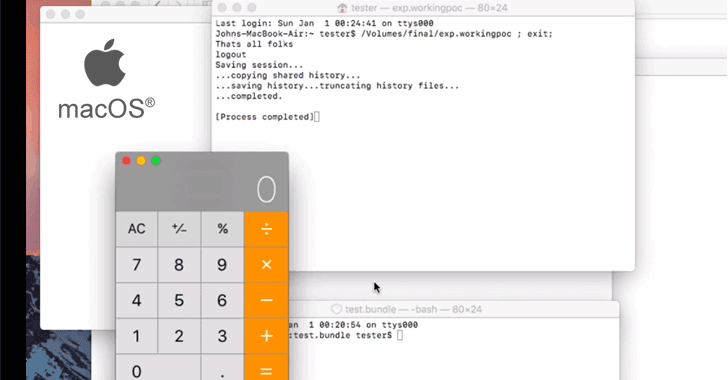
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...
[sc name=”ad_1″] Cheetah Mobile—a prominent Chinese app company, known for its popular utility apps like Clean Master and Battery Doctor—and one of...
[sc name=”ad_1″] The Department of Justice announced Wednesday charges against two Iranian nationals for their involvement in creating and...
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
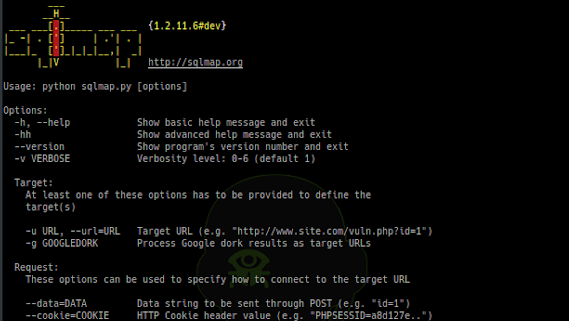
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...