[sc name=”ad_1″] Microsoft today issued an out-of-band security update to patch a critical zero-day vulnerability in Internet Explorer (IE) Web...
Search Results For - Embedded
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...
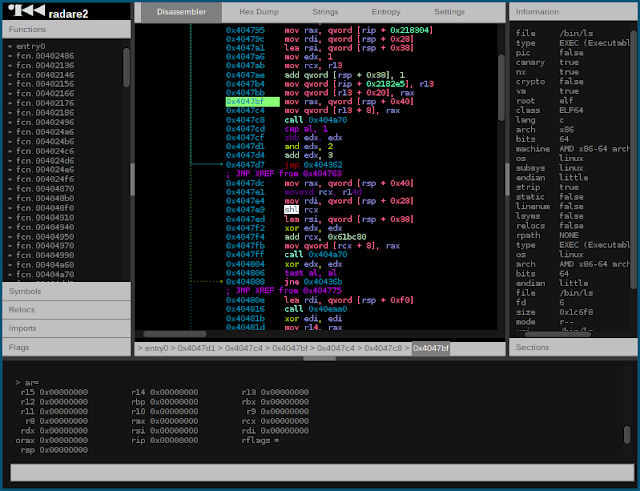
[sc name=”ad_1″] r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files. Radare...
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
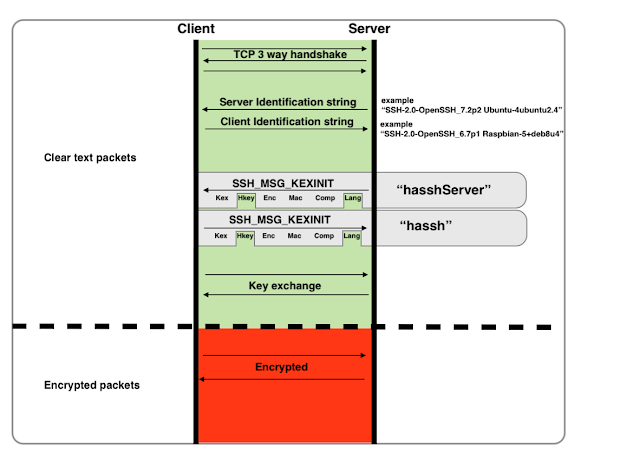
“HASSH” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be...
novahot is a webshell framework for penetration testers. It implements a JSON-based API that can communicate with trojans written in any language. By default...
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
Cybersecurity researchers have revealed an unpatched logical flaw in Microsoft Office 2016 and older versions that could allow an attacker to embed malicious...
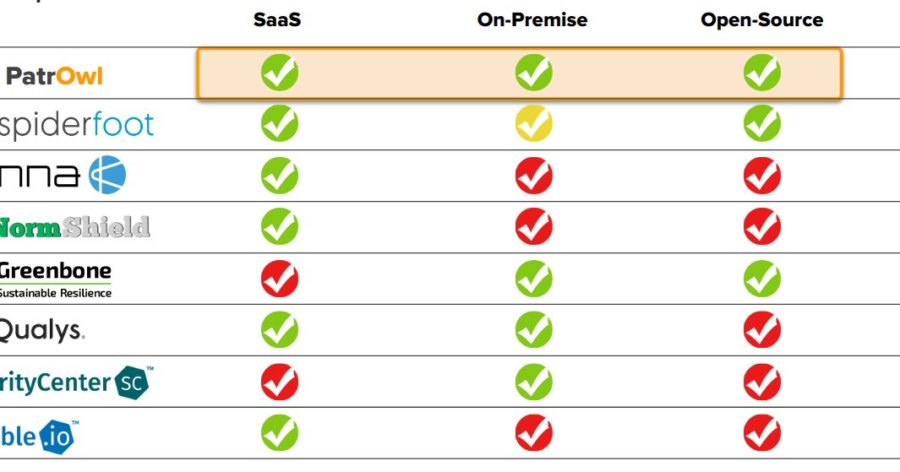
PatrOwl is a scalable, free and open-source solution for orchestrating Security Operations. PatrowlManager is the Front-end application for managing the...