Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...
Search Results For - Embedded
81 percent of data breaks last year involved weak, default or stolen passwords, and phishing attacks have advanced 65 percent year-on-year. Protecting online...
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
Smart Home Systems like the Google Home Mini is intended to only listen for a specific wake word, in this case, it’s “Hey Google” or “Ok Google.” Only then do...
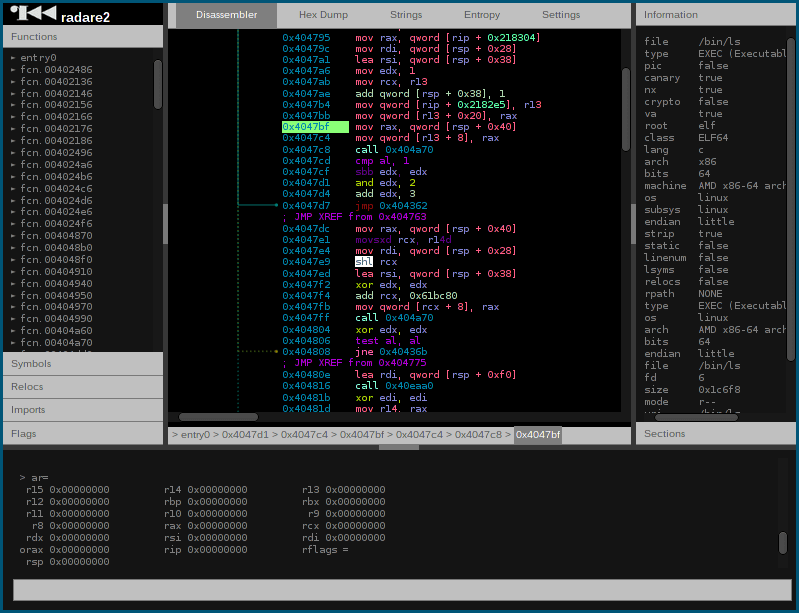
r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files. The radare project started as a forensics...