Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de...
Search Results For - Email
This type of abusive conduct is possible because of a configuration flaw in the login handlers included with all browsers, login managers that allow browsers...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
A security researcher has discovered a ransomware called Retis, which is a ransomware-type virus that secretly infiltrates the system. Shortly after executed...
Recent hacking events have stirred a controversy among the Canadian authorities. The past weekend, Ottawa police apprehended a teenage boy in a swatting case...
The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
The 2016 election hack is back in the news. With great efforts, a Russian hacker was arrested and upon interrogation, he revealed that he was hired by the...
On December 14, the company will vote to repeal the net neutrality practices it put in place in 2015. With Republicans agents who oppose the rules outnumbering...
It’s the latest movement in a clash between Amazon and Google, which has seen the two businesses hold their products off the rival’s programs and services...
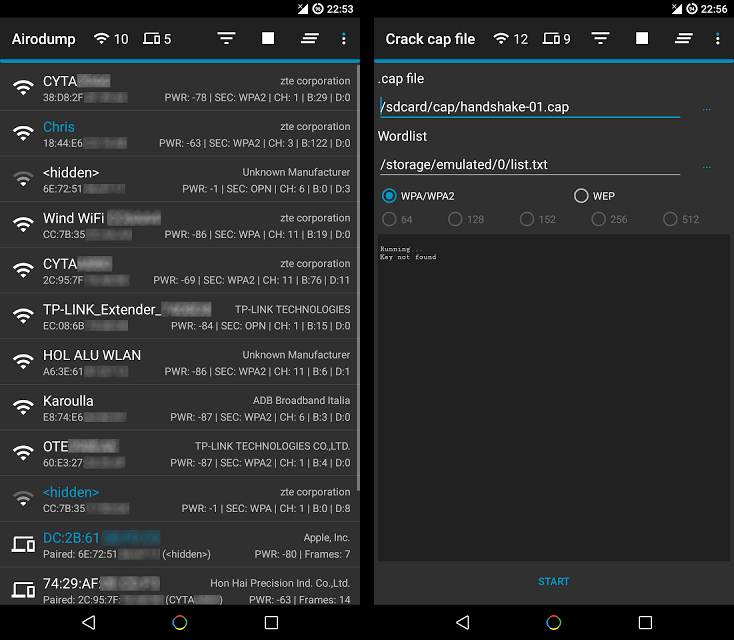
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...