[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
Search Results For - EXIST
[sc name=”ad_1″] A multi-threaded AWS inventory collection tool. The creators of this tool have a recurring need to be able to efficiently collect...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
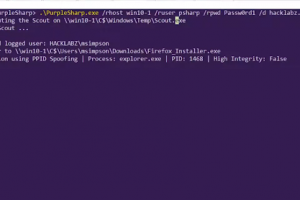
[sc name=”ad_1″] Defending enterprise networks against attackers continues to present a difficult challenge for blue teams. Prevention has fallen...
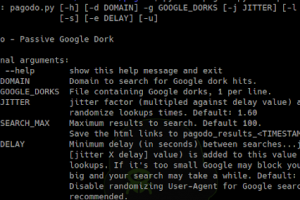
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
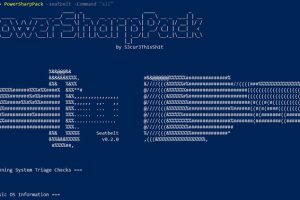
[sc name=”ad_1″] Many usefull offensive CSharp Projects wraped into Powershell for easy usage. Why? In my personal opinion offensive Powershell is...
[sc name=”ad_1″] Arcane is a simple script designed to backdoor iOS packages (iphone-arm) and create the necessar y resources for APT repositories...
[sc name=”ad_1″] Security Tool for Reconnaissance and Information Gathering on a website. (python 2.x & 3.x) This script use...
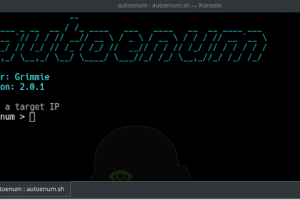
[sc name=”ad_1″] Autoenum is a recon tool which performs automatic enumeration of services discovered. I built this to save some time during CTFs...
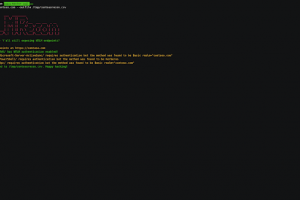
[sc name=”ad_1″] A fast and flexible NTLM reconnaissance tool without external dependencies. Useful to find out information about NTLM endpoints...