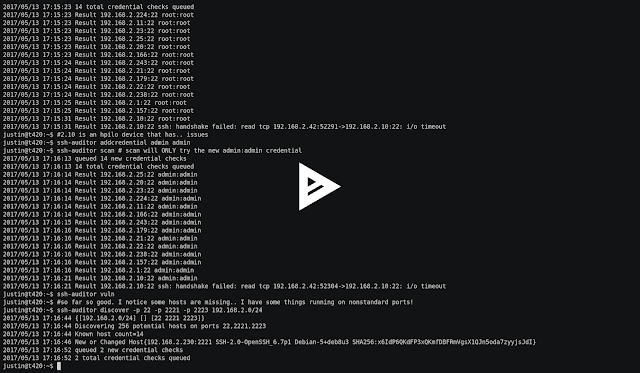
The Best Way To Scan For Weak Ssh Passwords On Your Network Features ssh-auditor will automatically: Re-check all known hosts as new credentials are added. It...
Search Results For - Default Credentials
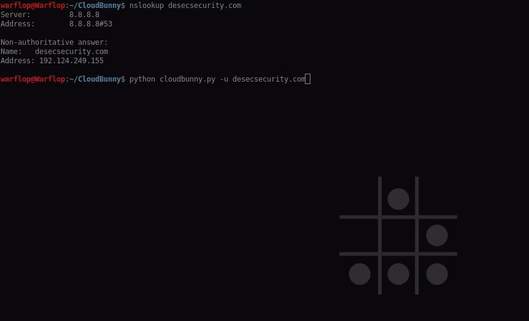
CloudBunny is a tool to capture the real IP of the server that uses a WAF as a proxy or protection. How works In this tool we used three search engines to...
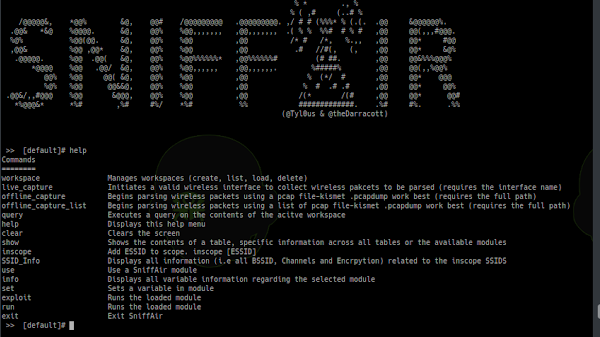
SniffAir is an open-source wireless security framework which provides the ability to easily parse passively collected wireless data as well as launch...
Console Application designed to interact with SharpSploit released by @cobbr_io SharpSploit is a tool written by @cobbr_io that combines many techniques/C#...
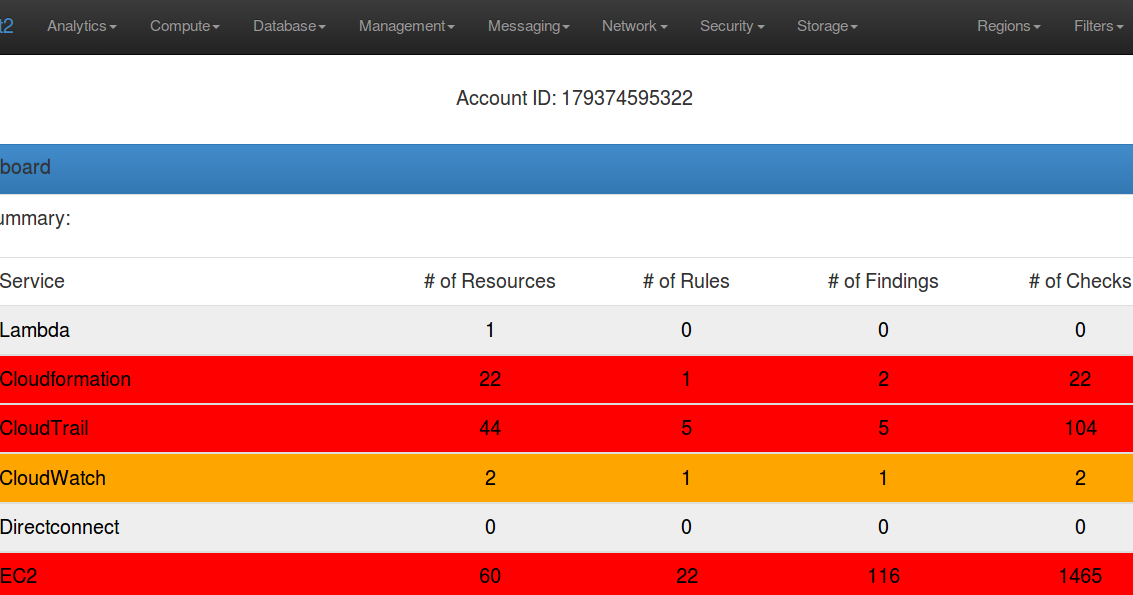
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
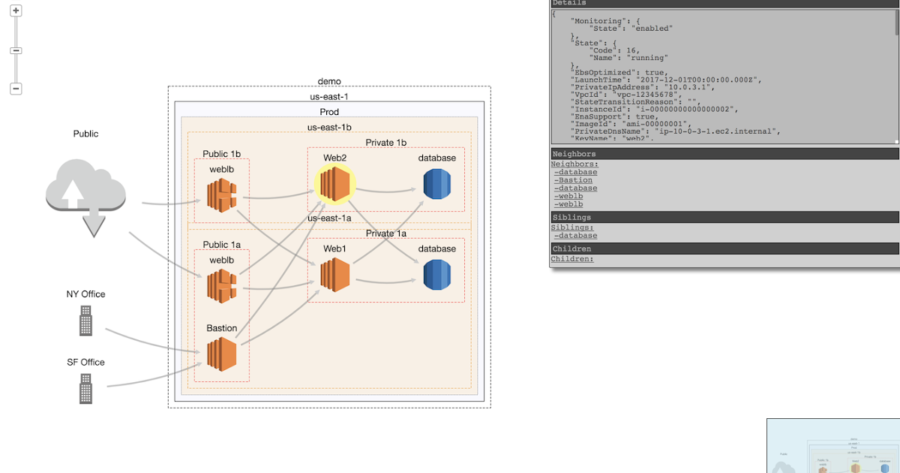
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your...
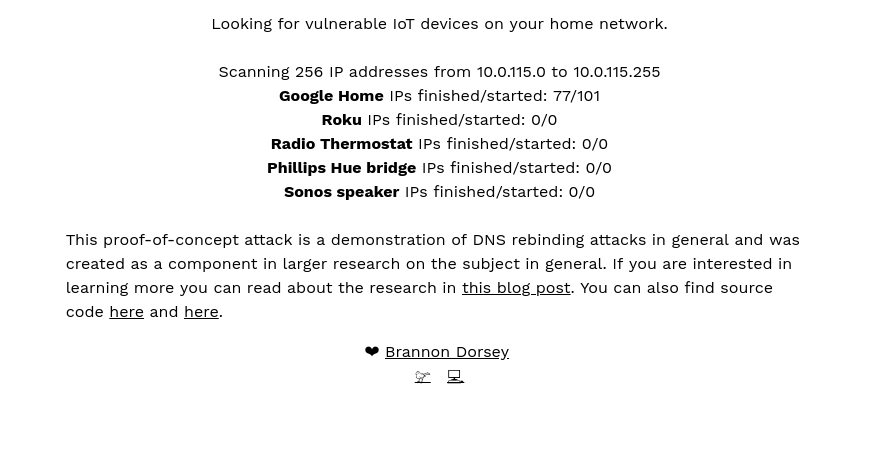
DNS Rebind Toolkit is a frontend JavaScript framework for developing DNS Rebinding exploits against vulnerable hosts and services on a local area...
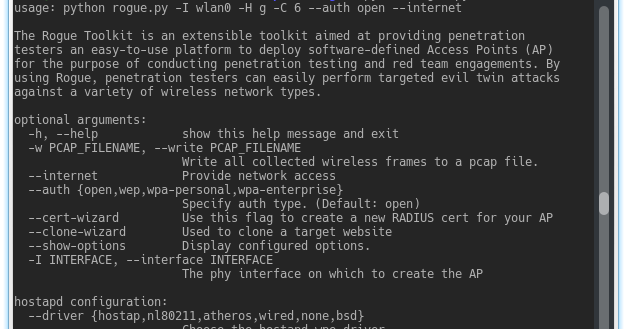
The Rogue Toolkit is an extensible toolkit aimed at providing penetration testers an easy-to-use platform to deploy software-defined Access Points (AP)...
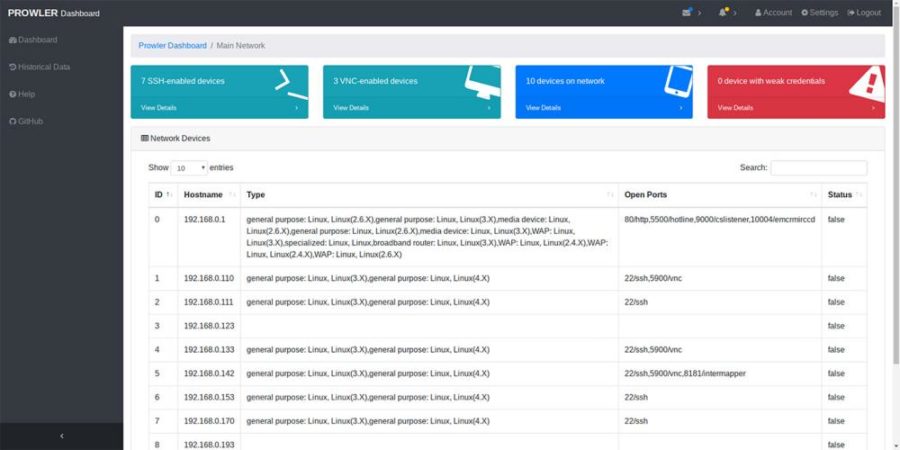
Prowler is a Network Vulnerability Scanner implemented on a Raspberry Pi Cluster, first developed during Singapore Infosec Community Hackathon – HackSmith v1.0...
The Rogue Toolkit is an extensible toolkit aimed at providing penetration testers an easy-to-use platform to deploy software-defined Access Points (AP) for the...