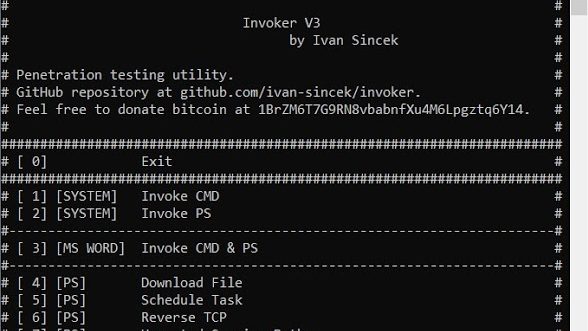
[sc name=”ad_1″] Penetration testing utility. The goal is to use this tool when access to some Windows OS features through GUI is restricted. Some...
Search Results For - DLL
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
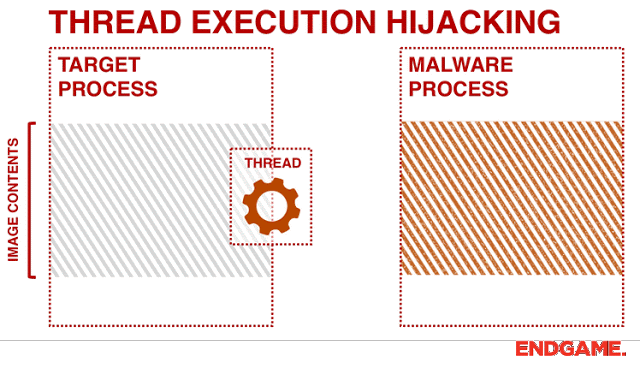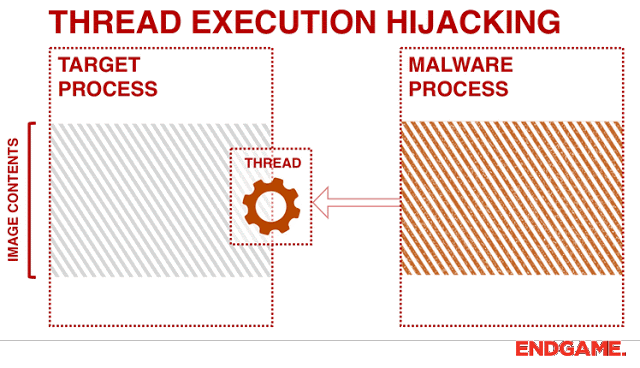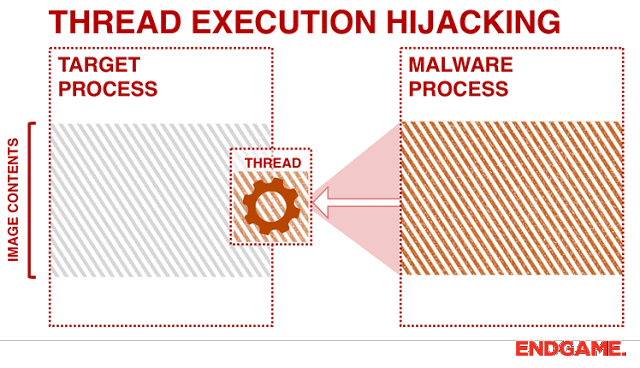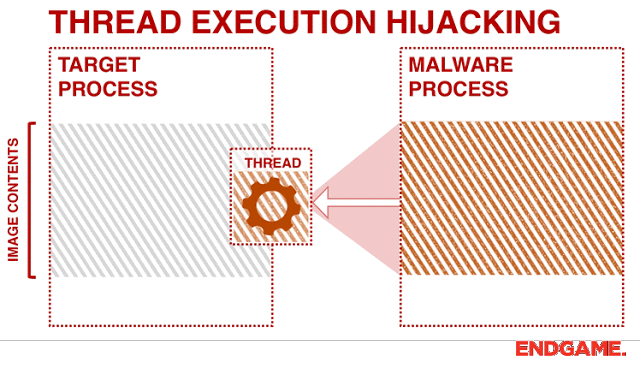
[sc name=”ad_1″] Program uses Thread Hijacking to Inject Native Shellcode into a Standard Win32 Application. With Thread Hijacking, it allows the...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
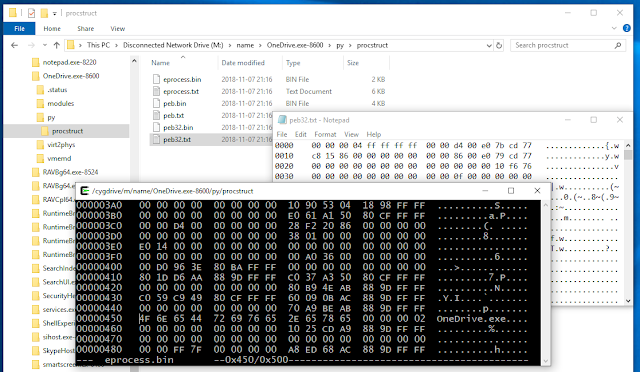
[sc name=”ad_1″] The Memory Process File System is an easy and convenient way of accessing physical memory as files a virtual file system. Easy...
[sc name=”ad_1″] Various cyber criminal groups and individual hackers are still exploiting a recently patched critical code execution vulnerability...
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] Beware Windows users… a new dangerous remote code execution vulnerability has been discovered in the WinRAR software...
[sc name=”ad_1″] A malicious Windows EXE file can even infect your Mac computer as well. Yes, you heard me right — a .exe malware on macOS...